Introducing AWS Security Services
AWS Security is critical in safeguarding the global infrastructure that powers all Amazon Web Services (AWS) cloud services. This infrastructure includes hardware, software, and networking components designed to ensure high availability and reliability. AWS Security protects this underlying cloud infrastructure, meeting industry security standards and compliance requirements. From data protection to threat detection and incident response, AWS implements best practices for maintaining the confidentiality, integrity, and availability of data. Through a shared responsibility model, AWS security services empower organizations to securely operate in the cloud while meeting stringent regulatory compliance needs.
Why Choose AWS Security Services?
-
Keeps Data Safe: Infrastructure incorporates strong safeguards to help protect privacy. All data is processed in highly protected data centres.
-
Meets Compliance Requirements: Manages dozens of compliance programs in its infrastructure. Organizations meet compliance effortlessly.
-
Saves Operational Cost: Operational cost is reduced as organizations don't have to maintain on-premise facilities.
-
Scales Quickly: Security scales with the organization's usage of Amazon Web Services Cloud. The architecture is built to keep data secure, no matter the size of the enterprise.
AWS Serverless Computing manages all the services that a user can use to build and run its program on it's system. Click to explore about our, Amazon Web Services Serverless Computing
Understanding AWS Security and Compliance Framework
AWS Cloud Compliance enables you to understand the robust controls in to maintain security and data protection in the cloud. The related enablers are built on traditional programs by combining governance-focused, audit-friendly features with applicable compliance or audit standards. This helps clients to establish and operate in an environment of Amazon Web Services security control. The IT infrastructure it provides to an organization is designed and managed in alignment with best security practices & a variety of IT security standards. A partial list of assurance programs Amazon Web Services complies with is as follows:
-
SOC 1/ISAE 3402, SOC 2, SOC 3 - AWS complies with SOC 1, SOC 2, and SOC 3 standards, which focus on data security, availability, confidentiality, and processing integrity. These reports are essential for organizations seeking to meet audit and compliance requirements for various financial and operational processes.
-
PCI DSS Level 1 - AWS meets the PCI DSS Level 1 requirements, ensuring that businesses using AWS for payment processing comply with the highest standards for secure handling of cardholder data. This is crucial for organizations in the payment card industry.
-
FISMA, DIACAP, and FedRAMP - AWS is compliant with FISMA and DIACAP requirements, allowing U.S. government agencies and contractors to store and process data in the cloud while adhering to federal security standards. In addition, AWS has been authorized under FedRAMP, which is a U.S. government program that provides a standardized approach to security assessment for cloud products and services.
-
ISO 9001, ISO 27001, ISO 27017, ISO 27018 - AWS holds a range of ISO certifications that showcase its commitment to global security and data protection best practices. These include:
- ISO 9001: Focuses on quality management systems.
- ISO 27001: Ensures comprehensive information security management.
- ISO 27017: Provides guidelines for information security controls for cloud services.
- ISO 27018: Ensures the protection of personal data in the cloud, particularly for PII (Personally Identifiable Information).
AWS Shared Security Responsibility Model
It is essential to consider how security in the cloud is subtly different from security in the on-premise data centers before discussing how its security works. Security obligations are exchanged with the organization and its cloud service provider as organizations transfer their operating systems and data to the cloud. In this case, It is responsible for securing the underlying infrastructure that supports the cloud. The organization is responsible for anything that you put into the cloud or connect to the cloud. This shared security responsibility model can reduce your operational burden in many ways and, in some cases, may even improve default security posture without additional action on your part.
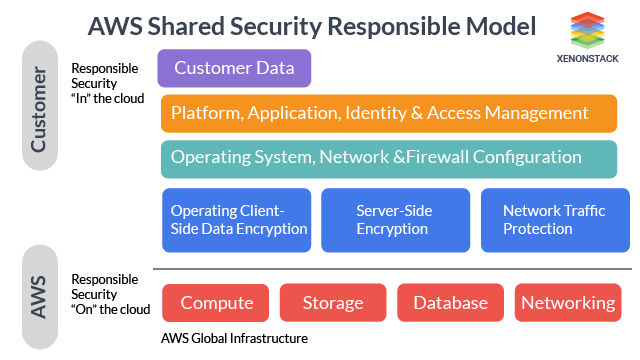 Fig 1: AWS Collaborative Security Responsibility Structure
Fig 1: AWS Collaborative Security Responsibility Structure
Inspired by the Shared Responsibility Model—Amazon Web Services—we think the amount of security configuration work you need to do depends on which services you choose and how sensitive your data is.
AWS Security Services Overview
AWS offers a wide range of security services to protect applications, data, and systems. These services ensure compliance, mitigate threats, and enable secure operations in the cloud.
Computer Services
-
Amazon EC2 Security
Amazon EC2 provides scalable compute capacity for hosting applications, with built-in security features to protect server instances. -
Auto Scaling Security
Auto Scaling adjusts the number of EC2 instances automatically, ensuring performance while reducing costs.
Networking Services
-
Elastic Load Balancing
Elastic Load Balancing distributes incoming traffic across EC2 instances to maintain application performance and availability. -
Amazon VPC Security
Amazon VPC enables organizations to create isolated network environments within AWS, enhancing security by using private IP addresses.
Storage Services
-
Amazon S3 Security
Amazon S3 offers secure, scalable object storage with encryption at rest and access control features. -
Amazon S3 Glacier Security
S3 Glacier is designed for low-cost, secure data archiving with customizable retrieval times. -
AWS Storage Gateway
Storage Gateway connects on-premises environments to AWS cloud storage, ensuring secure data integration. -
AWS Snowball Security
Snowball enables secure, physical data transfers to AWS for large-scale data migration, particularly in low-bandwidth scenarios.
Database Services
-
Amazon DynamoDB Security
DynamoDB is a fully managed NoSQL database offering fast performance with built-in security features like encryption. -
Amazon RDS Security
Amazon RDS allows easy provisioning and managing relational databases, ensuring automatic backups, patching, and encryption. -
Amazon Redshift Security
Redshift is a managed data warehouse service with advanced security features to protect petabyte-scale data.
Deployment & Management
-
AWS IAM
IAM provides fine-grained access control, allowing administrators to manage user permissions securely. -
Amazon CloudWatch Security
CloudWatch monitors AWS resources, providing insights into security events and system performance for proactive management.
AWS Identity and Access Management (IAM) is crucial for ensuring security and compliance in AWS by providing granular control over user access to resources. For a deeper dive into IAM best practices, explore Introduction to Identity and Access Management
Emerging Threats and Trends in Cloud Security
As cloud adoption continues to grow, so do the evolving threats targeting cloud infrastructures. While AWS provides a comprehensive suite of security services, organizations must remain vigilant in monitoring and responding to new and emerging threats. Below are some of the most notable trends and threats impacting cloud security:
-
Increased Sophistication of Cyberattacks
Cyberattacks are becoming increasingly sophisticated. Attackers utilize advanced techniques such as phishing, ransomware, and AI-driven exploits to target vulnerabilities in cloud systems. Cloud infrastructures, including AWS, must be continuously fortified to prevent breaches and ensure data protection. -
Supply Chain Attacks
One of the emerging threats in cloud security is the rise in supply chain attacks. Hackers target third-party vendors, software, or services integrated with cloud environments to infiltrate the system. This highlights the importance of securing every layer of your cloud ecosystem, not just your AWS infrastructure. -
Misconfigured Cloud Resources
Misconfigurations remain one of the top reasons for cloud security incidents. A simple misconfigured Amazon S3 bucket or improper AWS Identity and Access Management (IAM) roles can lead to data exposure or unauthorized access. Automated tools like AWS Config and AWS CloudTrail help identify and mitigate configuration errors. -
Zero-Day Vulnerabilities and Exploits
The cloud environment is not immune to zero-day vulnerabilities. Attackers often exploit previously unknown vulnerabilities in cloud services or customer configurations. Therefore, it is crucial to stay up to date with AWS security patches and conduct regular vulnerability assessments. -
Insider Threats
Insider threats pose a significant risk, particularly in large organizations with complex cloud infrastructures. AWS’s granular IAM policies, such as enforcing multi-factor authentication (MFA) and implementing the principle of least privilege, can significantly reduce the risk of insider threats.
Best Practices for AWS Security Configuration
To maintain a strong AWS security posture, organizations should follow these key best practices:
AWS handles cloud infrastructure security, while customers secure their data, applications, and configurations.
Enforce strict access control with AWS IAM, applying the principle of least privilege to limit permissions.
Activate MFA for both root and IAM users to prevent unauthorized access, even if credentials are compromised.
Use AWS services like S3, EBS, and KMS to encrypt data at rest and in transit, ensuring sensitive data is secure.
Enable AWS CloudTrail to log and monitor account activity, detect unauthorized access, and maintain a security audit trail.
Use VPC to create secure, isolated environments by segmenting resources and applying security groups and ACLs.
AWS Security Checklist
Follow the AWS Security Checklist below to enhance your security to the maximum level.The Starting List
- Log across all AWS services, validate log files, activate multi-region logging, and integrate with CloudWatch.
- Enable logging for CloudTrail S3 buckets, Elastic Load Balancer (ELB), Redshift audit logs, and VPC flow logs.
- Require MFA for deleting CloudTrail buckets, root accounts, and IAM users.
- Link IAM policies to groups or roles, enforce a strict password policy (90-day expiration), and regularly rotate IAM access keys.
- Use HTTPS for CloudFront distributions, avoid expired SSL/TLS certificates, and encrypt CloudTrail log files and Elastic Block Store (EBS) databases.
- Provision access using IAM roles, avoid using root user accounts, and apply standard naming conventions for EC2 instances.
The Ending List
- Apply secure ciphers for client-ELB connections and use secure SSL versions between ELB and clients.
- Encrypt Amazon RDS and ensure access keys are not used with root accounts.
- Periodically rotate SSH keys, terminate unused access keys, and remove inactive IAM users.
- Minimize discrete security groups and IAM groups; limit access to AMIs, EC2 security groups, RDS instances, Redshift clusters, and outbound access while disallowing unrestricted ingress on uncommon ports.
- Involve IT security throughout development and grant minimal privileges to application users.
- Encrypt sensitive data such as personally identifiable information (PII) or protected health information (PHI).
Key Takeaways: AWS Security Services and Their Impact
AWS Security Services are a must for catering security for enterprises employing them. We also provide Azure Security Services and GCP security solutions. With features like robust compliance, scalable security, cost savings, and the AWS Shared Responsibility Model, organizations can efficiently manage their cloud environments. These services empower enterprises to maintain operational resilience, meet regulatory requirements, and protect sensitive data.
AWS also provides specialized tools across computing, networking, storage, and database services to enhance cloud security at every layer. Companies can further strengthen their security posture by following best practices, such as encryption, IAM policies, and continuous monitoring. AWS Security Services, alongside complementary offerings from Azure and GCP, are essential for any enterprise committed to building a secure, scalable, and compliant cloud infrastructure.
- Discover more about Cloud Managed Services
- Explore More about Kubernetes Managed Platforms
- Know More about Managed Security Services
Next Steps
Talk to our experts about implementing AWS Security Services and Compliance. Discover how industries utilize AWS to enhance security and meet regulatory requirements. Leverage tools like AWS Security Hub and AWS Config to automate compliance processes, improve efficiency, and ensure robust data protection in the cloud.