This is complicated because threat vectors are rising, and SOCs are a vital protective element in cybersecurity. Alerts are increasing in number and proportion, and the types of attacks are getting more complex, making it difficult for a human analyst to manage them effectively. Since most conventional SOCs require human intervention, several problems, such as scalability and accuracy, may occur.
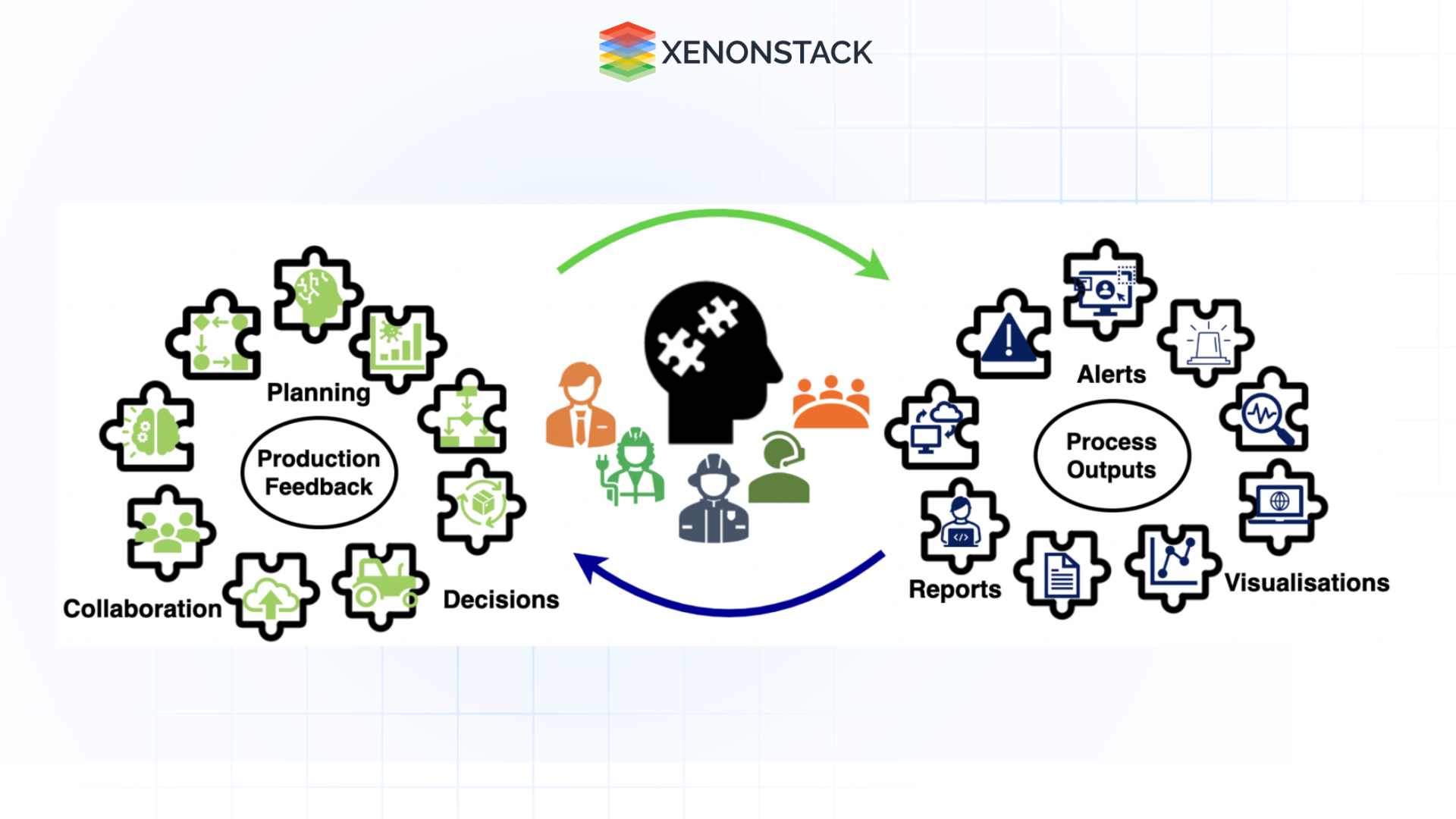
Figure 1: Human-in-loop in visual analytics
To counter these issues, most SOCs are now looking at automating the whole process with the help of SIEM systems, SOAR platforms and AI tools. Although automation improves the general performance of systems, there is a weakness when dealing with complicated threats. This is where human-in-the-loop (HITL) automation fits: integrating human and intelligent systems to make the best decisions and input. In this blog, we will discuss the following aspects: How HITL is revolutionizing the SOC automation process, the advantages and disadvantages of HITL and the use cases.
What is HITL in SOC Automation?
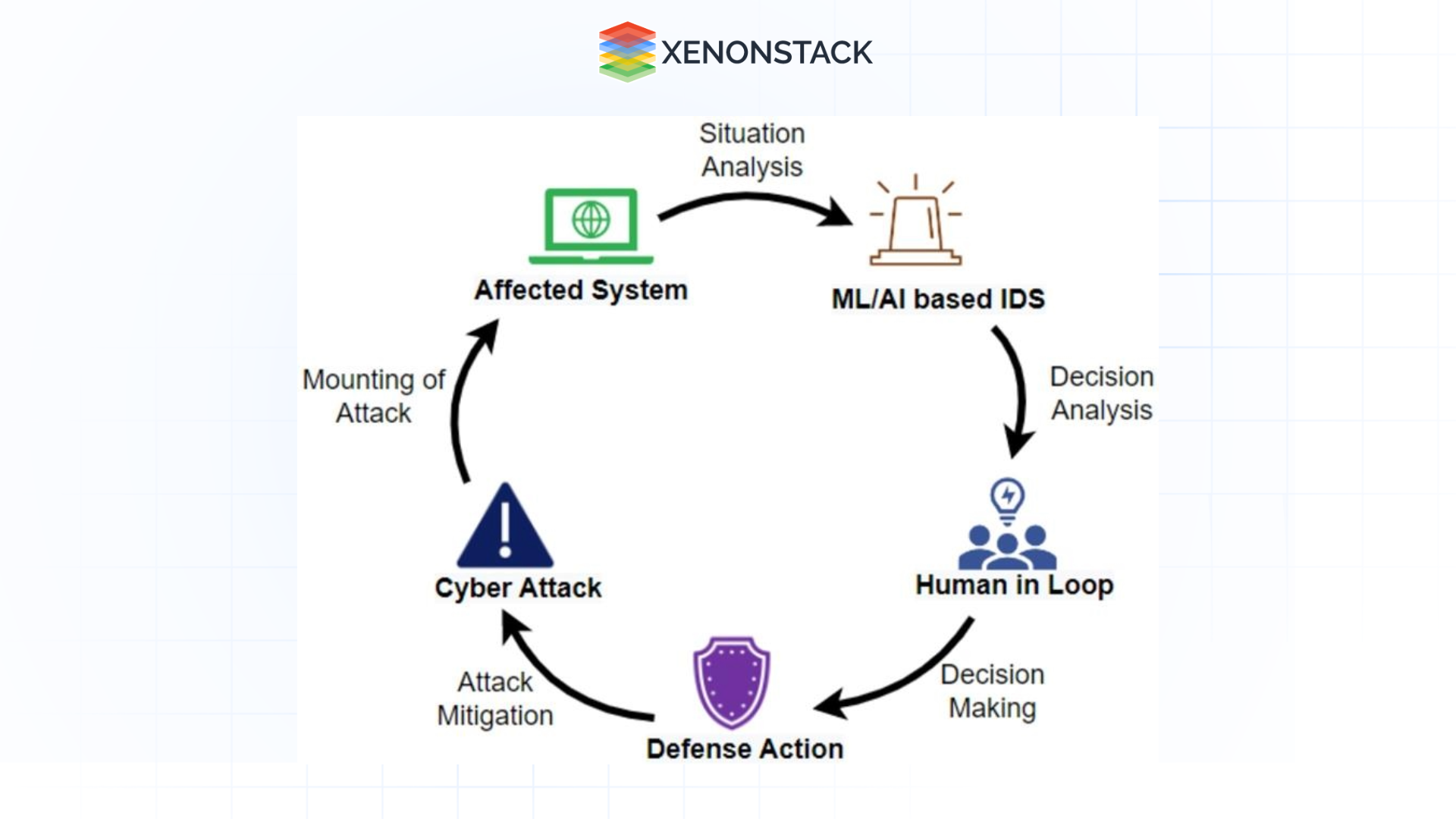
Figure 2: Human-in-loop in hybrid intelligence
Human-in-the-loop (HITL) is an approach in which certain tasks are executed depending on human interaction to derive improved, circumstance-sensitive, and efficient decisions. In the context of SOCs, HITL is the approach that engages technology to perform duties like recognizing threats, sorting through alerts, and responding to incidents, with analysts having the distinct responsibility of critical decision-making and supervising. For instance, the SOC system helps identify an anomaly that requires automation to take basic interventions such as disconnecting such systems or giving out an alert. However, experienced human beings oversee these actions and make decisions based on their knowledge and experience of the organization and threat.
With this approach, we assure you that automation will handle large amounts of data and repetitive tasks. At the same time, human analysts will provide creativity, judgement, and insightful experience in handling complex security incidents.
Why is HITL Important in SOC Automation?
Figure 3: Human-in-the-loop example in training AI models to classify objects
Despite the capabilities of automation in SOCs, there are several reasons why human involvement is necessary:
-
Complex and Evolving Threats: Traditional automation tools are very good at identifying known patterns of attack, but they can fail to identify unknown or new patterns of attack, which are the kinds of attacks that are difficult to detect, such as zero-day exploits or APTs. HITL guarantees that, for these advanced threats, a human being can step in and filter them and work out new tactics, techniques, and procedures.
-
False Positives and False Negatives: Automated systems represent high speed but lack efficiency and are not completely precise. They can produce a response that alerts normal activities as threats, known as false positives, and a type that does not alert to actual threats, known as false negatives. These alerts call for human analysts to come in, strain out the noise, and ensure that real threats are not missed.
-
Context and Nuance: Threats in cybersecurity are usually complex and require analysis of the surrounding context. Self-driving systems cannot learn all the detailed information concerning the organizational environment or risk tolerance. In the case of HITL, human analysts can help identify threats in their context and based on business needs and market conditions.
-
Compliance and Legal Considerations: Secured incidents typically involve personal information, and thus, SOCs must address legal frameworks like GDPR, HIPAA, and the like. Legal factors are essential during an incident, and because of this, human analysts can analyze these aspects and guarantee that actions throughout an incident are legal.
-
Scalability with Control: SOCs must grow to handle a constantly increasing number of security events, and dependency on automation is an issue concerning the manageability of the results. HITL helps strike a middle ground as many incidents can be automatically processed. At the same time, a human can exercise control and make proper decisions during critical events.
Categories of HITL in SOC Automation
Figure 4: Human-machine collaboration in Industry
The application of HITL in SOC can be observed in several of the main operational fields of SOC organizations. Below, we examine how automation and human intervention can complement each other at various stages of the cybersecurity lifecycle:
-
Threat Detection & Alert Triage: In SOCs, solutions like the SIEM platform produce alerts from indicators such as network traffic, log data, etc. Conversely, although these systems can recognize patterns of interest quite rapidly, there are often too many alerts for human analysts to digest. This is where automation assumes a vital function of sorting out noise and directing attention towards true alarms so analysts can focus on incidents.
However, automated systems have the disadvantage of not understanding the alerts in the right context. For example, an alert that may look very risky might be caused by the wrong configuration of the network. In those circumstances, some inputs must be handled by a human being to review the context, analyze it further, and determine if there is a threat.
-
Intention and Injury & Analysis: When a threat has been identified, other systems can gather information, correlate it, and include logs, system states, and threat intelligence feeds. However, an automated system may not be able to dissect the comprehensiveness of the attack or evaluate its effects on the organization.
At this step, human analysts can examine the data in detail, investigate further, and correlate data from one system or endpoint to another. For instance, when an alert for a suspicious file is raised, an automatic mechanism might quarantine the file. Still, an analyst must determine where the file has come from and other systems that may be related to it or part of a bigger attack.
-
Incident Response & Remediation: Most SOCs use automation to respond to basic incidents based on pre-scripted response templates. For instance, the infected system is isolated whenever malware is found, the malicious IP is denied, and the security team is informed. This automation promotes quick response and ensures that basic containment actions are taken immediately.
However, human analysts must respond to more intricate incidents to ‘provide a more comprehensive global incident response’. For instance, an insider threat, data leakage, or theft case may need human intelligence to engage legal, compliance, and IT departments to solve. The analyst decides whether broader containment measures are required–switching off systems or informing executives.
-
Threat Intelligence and Threat Analysis: While threat intelligence feeds are categorized as sophisticated threat feeds, they can produce valuable data regarding ongoing campaigns, attacks, and known attackers. Automation systems can sort through and sift out this intelligence, but analyzing the intelligence gathered necessitates human input.
HITL can, therefore, be used to enrich threat intelligence to make it more meaningful by letting human analysts give insights, correlate threat indicators with existing incidents and prioritize Intelligence to reflect the organization's risk appetite. For example, a threat intelligence report can point towards an attack on a certain vulnerability. At the same time, a human being can decide if this vulnerability is present in an organization and how crucial it is.
-
Performance Analysis of an Incident: Upon solving conflict or after an incident has occurred, HITL is highly involved in reviewing the execution and source of the conflict for upcoming references. Structural systems may be used to produce automatic operational reports over recorded incidents. In contrast, structural analysts are crucial in fine-tuning the approaches used in the response, determining the causes of vulnerabilities, and elaborating on security features.
Lastly, evaluation after the event may result in examining organizational reputation or legal and compliance issues. Having human analysts makes it possible to pay attention to detail regarding documentation of all aspects of the incident and ensure that the lessons learned when developing subsequent security objectives are implemented.

-
Enhanced Specificity and Lowered Sensitivity of the Assay
Using robotics in this analysis minimizes the possible error rates of false positives and false negatives of HITL. Most activities are computerized to reduce costs and social-engineering attacks, but the computer findings are reviewed by an analyst before escalation.
-
Operating efficiency; high productivity
HITL helps manage low-priority requirements, like log analysis, alert acknowledgements, and initial assessments so that SOC analysts can be wholly dedicated to incidents. This results in high efficiency and effectiveness since the SOC will be able to handle as many threats as it did when it was small but will produce quality work.
-
Enhanced Threat Detection
HITL enhances threat acknowledgement and detection outcomes by integrating the power of automation and human analysts' heuristics. While an automated system detects patterns and sets an alert, a human’s brain must interpret the alert and understand that it is derived from an advanced or novel attack strategy.
-
Better Decision-Making
Some situations in SOCs demand judgment, experience, or business perspective, qualities that automatic control lacks. HITL lets human analysts determine an adequate response level depending on the degree of dangerousness and type of incident.
-
Scalability and Flexibility
Soc automation enables SOCs to scale properly, but in most cases, it requires supervision from expert personnel. HITL helps SOCs manage more incidents as the organization grows and allows analysts to manage priority cases and intricate procedures.
.webp?width=1921&height=622&name=usecase-banner%20(1).webp)







