Security Operations Centres (SOCs) are central to an organization’s cybersecurity function because they are responsible for analyzing, researching and mitigating security threats. But, as threats evolve into highly sophisticated and multiform, conventional surveillance and analytical approaches frequently fail to provide adequate solutions. Threat intelligence reports, security alerts, and incident logs produced in large numbers daily create congestion and alert fatigue for SOC teams. That’s where Natural Language Processing (NLP), an artificial intelligence technology, comes in and can interpret language. By helping concurrently examine large data content through textual data, NLP allows SOCs to identify patterns, extract valuable knowledge and accelerate the response.
Cyber security and Language Processing
Cybersecurity primarily works with an extremely high volume of text data in the form of alerts, logs, threat Intel feeds and so on. The focused and relevant data needs to be analyzed manually, and it is not only a time-consuming and extremely tiring process but poses the risk of producing results laden with human errors. A subset of AI known as NLP helps SOCs analyze the information for pertinent content and gain insight from lightweight text in a very short amount of time. 
Key Areas of NLP in SOCs

Threat Intelligence Analysis
Using NLP, SOCs can quickly parse through TI reports from various sources. The information that can be presented and filtered includes IoCs, attack-phenotype, and actor data.
Incident Response Automation
In the case of SOC teams, chatbots powered by NLP can help provide responses and answers to questions related to an incident and suggest a general approach to remediation based on historical evidence.

Alert Triage and Prioritization
The applied NLP algorithms filter alerts to display only the most severe ones and otherwise minimize the noise level, the misinformation that researchers need to work with.

Sentiment and Context Analysis
SOC uses NLP to scan through communication within the organization or on social networking sites to detect any sign of a team member becoming a threat.
Core NLP Techniques for SOCs
-
Named Entity Recognition (NER): This technique focuses on the recognition and categorization of objects like IP address, domain name, e-mail address, malware name, and the name of a threat actor's group within the text data. SOs find NER useful for discovering IoCs, actors, and pointed targets expressed in threat intelligence feeds, thus allowing for quicker and more accurate responses by SOCs.
-
Topic Modeling and Document Classification: This technique categorizes text messages into relevant categories, such as malware reports, phishing alerts, or vulnerability assessments. It aids in the flow of large volumes of data to the SOC, the sorting of incidents, and the ease at which the prevalent threats within the environment are identified.
-
Sentiment Analysis: Sentiment analysis describes the attitude of a conversation in social media, news or group/organization internal communication. It is especially helpful in pinpointing the beginning of reputational loss after a breach or uncovering an insider threat via negative sentiment in intra-organizational messages.
-
Text Summarization: In written form, NLP can also prove useful in shortening the time spent reading threat reports, incident logs, or security news by presenting its main points so that the analyst does not need to go through long documents. Utilities based on natural language processing compress large amounts of text into brief analyses to aid SOC teams in prioritization.
-
Machine Translation: In global organizations, particular security incidents could concern threats coming from certain countries and, as a result, be reported in specific languages. Further, by deploying machine translation SOCs can understand documents and threat intelligence in foreign languages instantaneously and respond to threats instantly.
Applying NLP in SOC Processes 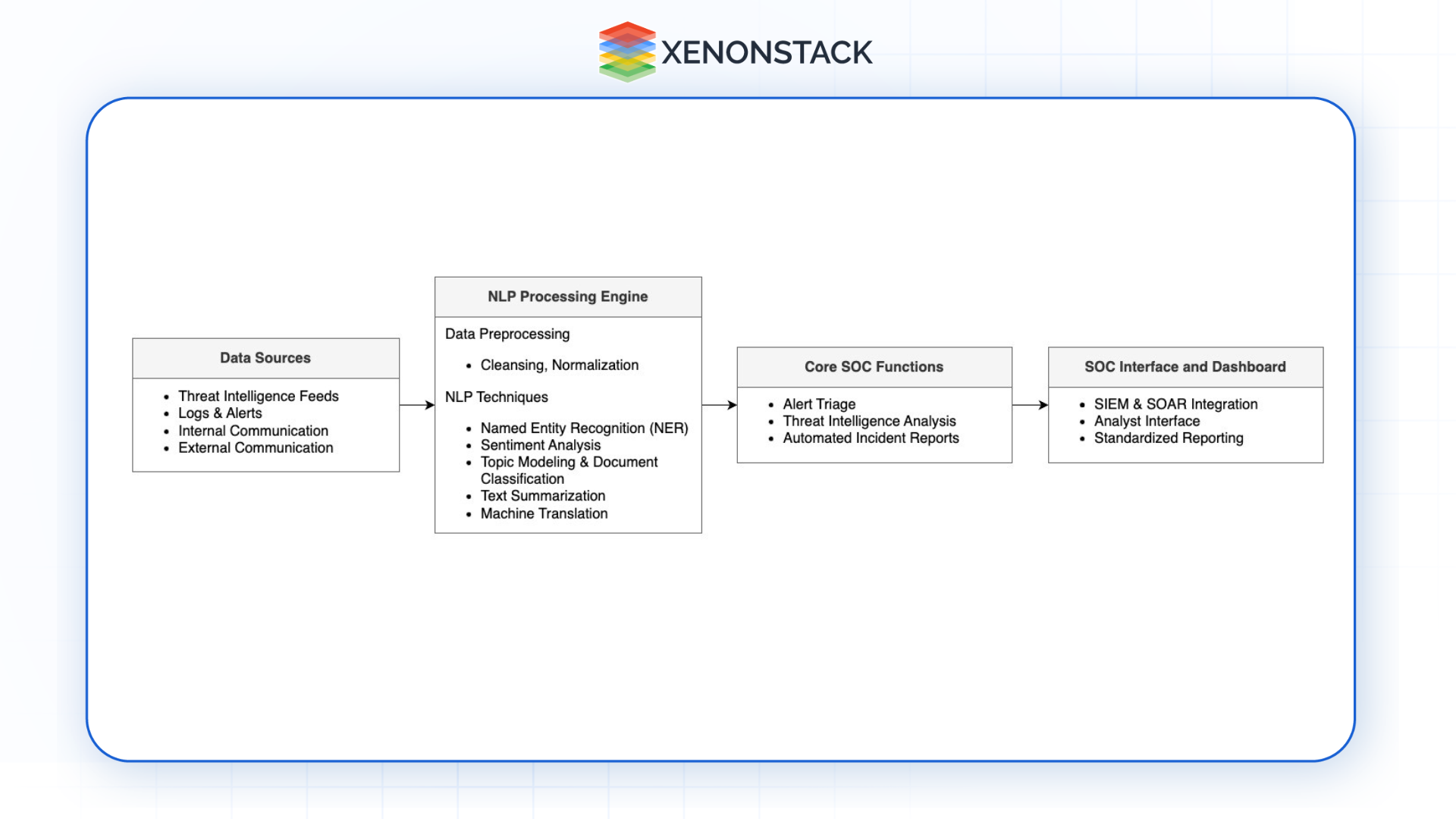
In SOC operations, NLP’s methods are used in the actions carried out in threat intelligence, incident handling, and response management. Here’s how NLP contributes to various SOC processes:
Automated Threat Intelligence Processing
Threat intelligence may come from different external sources and internal SOCs. Such reports can also be analyzed using NLP tools, and the IoCs and other necessary information can be collected on autopilot. This intelligence is then used by the SOC SIEM or SOAR, which stands for Security Information and Event Management, Security Orchestration, Automation, and Response platforms.
Alert Prioritization
SOCs receive numerous alerts daily, often rear digits or considered such. NLP models can assist in such manners by sorting the alerts, categorizing them, tagging the crucial information, and evaluating the real threats and their merits, of course, based on risk level. This makes it easy for SOCs to visualize top incidents and leave behind trivial incidents with alert fog.
Automated Incident Reports
Automatic systems can apply natural language processing to parse the information contained within the incident reports to produce analyses of the relevant attack patterns and the techniques employed and systems exploited. It confirms that such reports offer periodic information concerning the involvement and occurrence of incidents that assist in formulating prevention techniques. Automated reporting also helps prevent cases where some are usually poorly documented and others well recorded.
Response Coordination with NLP-Powered Chatbots
Chatbots can also integrate NLP into the work of SOCs by answering analysts’ questions on how to proceed further, giving advice on what actions can be taken in the context of the specific incident, and answering other related or general questions. They eliminate frequent reliance on senior staff, offer prompt assistance for normal-type occurrences, and allow analysts to address more occurrences.
Threat Actor Profiling
Through analysis of threat reports and domestic, international, and dark Web data, SOCs can build complete profiles of specific threat actors. This, in turn, enables the creation of enhanced threat intelligence and the comprehension of adversary TTPs.
Benefits of NLP in SOCs
-
Improved Efficiency: SOCs do not need to spend much time sifting through vast amounts of data since NLP reduces data processing time. SOC analysts can then focus on high-priority tasks, leaving the routine processing to NLP tools.
-
Enhanced Incident Detection: The tool makes SOC more effective in identifying incidents than ever by analyzing threat intel reports, logs, and alerts. This early detection capability is really important for quick reaction and preventing losses.
-
Reduced Analyst Fatigue: Through learning, the NLP system is capable of improving the filtering process, as well as organizing the prioritization of the alerts to minimize false positives and in turn cut down on alert fatigue. SOC analysts are able to immediately see the more dangerous and greater threats rather than being bombarded with alerts on unimportant things.
-
Better Threat Intelligence: NLP helps SOCs assimilate different forms of threat intelligence data to improve threat coverage and proactive security stance.
-
Standardized Reporting: Automated reporting, in turn, comprises summaries of incidents, which are completed and error-free due to NLP processing.
Difficulties of Integrating NLP in the SOCs
 Figure 3: Illustrating challenges faced in integrating NLP with existing systems
Figure 3: Illustrating challenges faced in integrating NLP with existing systems -
Data Quality and Preprocessing
Different NLP models require other text data types in their training and application. Security data, typically heaped and consisting of loosely structured information in large quantity, might take a lot of time to prepare before it can be analyzed through NLP. -
Complexity of Cybersecurity Language
There is a specific lexicon that belongs to the domain of cybersecurity, consisting of abbreviations and terms of art. Teaching the NLP models the details of cybersecurity discourse is a very difficult process that demands perfect data selection and deep knowledge of the cybersecurity field. -
Privacy Concerns
Communications used for insider threat factors or sentiment analysis may be sensitive to an individual’s privacy. In their original recorded form, it must be ensured that while deploying NLP implementations, SOCs meet the aspects of privacy regulations such as GDPR. -
Language Diversity
Global organizations must analyze threat reports in the source, English, and sometimes other languages. The translation must be effective, although it might not always be accurate in technical language. -
False Positives
False positives are easily observable when using the NLP models, especially when the system is in anomaly detection mode. These errors must be wiped out to enhance the appropriateness of the alerts given by the SOCs; hence, models must be enhanced with time.
Solving the Top NLP Problems in Security Operations Centers
-
Data Cleaning and Enrichment: Prepare the text data to enhance quality by cleaning it and normalizing the terms used. Specifically, the type of enrichment, such as tagging specific known IP addresses or domains, increases NLP performance.
-
Domain-Specific Training: Use Cyberspecific NLP models from data belonging to this domain so that the models generated can easily understand cybersecurity terminologies.
-
Integrate Human Review: NLP should be used for initial screening, but the human analyst should be involved in decision-making, given that these are high-risk incidents or possibly involve sensitive information.
-
Continuous Model Updates: You must train your NLP models with new threat data to minimize false positives. The model should also be able to adapt to the continually changing threat landscape.
Real-World Application of NLP for SOC
Threat intelligence analysis at IBM X-Force IBM’s X-Force Threat Intelligence team said they leverage NLP for processing threat intelligence reports to identify trends and extracting IoCs to enrich their database. This makes it easier for their SOC teams to understand threats and to act quickly if there is likely to be an incident.
Reducing False Positives at Palo Alto Networks Cortex XDR is an autonomous system that uses NLP to examine all security alerts and filter out the noise. This paper also shows how context and critical alert identification enhance response activities within a SOC platform and reduce noise that otherwise lingers around threats.
SOC Chatbots by Microsoft Azure Sentinel incorporates natural language processing chatbots to help SOC analysts. They allow users to identify popular questions and navigate the subsequent steps in incident triage, which saves the time of less experienced analysts.
At Recorded Future, Threat Actor Profiling records threat actor activities using NLP across the dark web and other open sources. Considering the language used by threat actors, NLP algorithms get insights into how they operate to understand their strategies and identify the most vulnerable targets for an attack; hence, SOC can prevent them effectively.
For this reason, NLP mimics advanced SOCs in the sense that it assists them in better handling modern issues in cybersecurity. Through threat intelligence analysis, alert first-stage assessment, incident handling, and threat characterization, NLP enables SOC analysts to prioritize high-value tasks alongside improving the SOC’s timeliness. Despite this, there are still open problems for NLP, which needs better data quality and domain-oriented training; however, the next-generation SOC cannot be imagined without the continued development of NLP. NLP-based SOC is becoming more popular in organizations, and as the volume and sophistication of threats increase, organizations will be more prepared for the risk.
Next Steps: NLP in SOC
Talk to our experts about implementing Natural Language Processing (NLP) in SOC. Learn how industries and departments use NLP-powered workflows and decision intelligence to become decision-centric. NLP helps automate and optimize security operations, enhancing threat detection, incident response, and overall efficiency in IT support and operations.