Introduction
DevOps demands work culture modification, and different metrics are required to measure DevOps culture. Do you know, How frequently are systems audited for compliance with various policies? How are organizations protecting their sensitive data? How long does it take to remediate a failing control or vulnerability?
Cloud is dynamic and complex - resources are added, deleted, or reconfigured to meet the client's requirements. Therefore, enterprises need to keep track and stay updated to meet the organizational requirements. It is hard to keep updated with the changing regulations while ensuring continuous compliance and remediation.
What is Continuous Compliance?
Continuous compliance is a technique of continuously monitoring IT assets to verify that they meet regulatory security requirements. It continuously searches networks for threats. You will be notified immediately if an IT asset is non-compliant. Therefore, you can maintain a tight security posture with no response delays, and you can minimize hazards right away.
Continuous compliance leads to immediate success by eliminating the need to spend countless hours collecting evidence. Continuous compliance is a proactive approach that helps to simplify the process of tracking security risks in real-time.
The Need for Continuous Compliance
Security and compliance are more crucial than ever today, as distributed environments continuously add new points of vulnerability. Moving into an environment of non-compliance and vulnerability exposes organizations to both regulatory and security risks, with effects ranging from fines and sanctions levied by regulators to interrupted processes, compromised data, and financial loss. What is needed is an approach for the best practices that enable the organization to demonstrate compliance while enhancing security continuously.
Therefore, an ongoing process is required to monitor the assets that ensure compliance with regulative security benchmarks. It continually scans the networks to detect the threats/risks. Instant notification is received whenever a non-compliant IT asset is detected. The detected risks can be mitigated immediately by maintaining a secure security posture with no delays.
Continuous Compliance in DevOps
Having compliance-driven culture helps the organizations to reduce risks, operational costs and also helps in improving efficiencies. Some standard practices for continuous compliance are:
Early Integration
Any compliance activity should be included in the initial stage of the software development lifecycle, as it is not a good practice to leave the compliance-related and security concerns for the later stages. Integrating this will not remove all the issues related to compliance, but surely it will enhance the quality, stability, security, and agility of the software.
Maintain Audit Trails
Maintaining the audit trails of the development activities is the most crucial requirement for continuous compliance. It will track and log every change made to the source code, which may also help the organizations in disaster recovery.
Continuous Testing
Continuous Testing can be done with continuous deployments. We should monitor all the activities to detect unauthorized requests easily. This automation process also increases the security posture of the organization.
Automated Scaling of infrastructure
With the implementation of continuous compliance and codified configurations, it is easy to monitor your infrastructure at scale. Therefore, you can dynamically enforce compliances and monitor the reconfiguration of your infrastructure in an automated way. Hence, Notify the developers for all the non-compliant resources in the early development environment, which can then be made compliant, increasing overall performance and productivity.
Compliance as a code
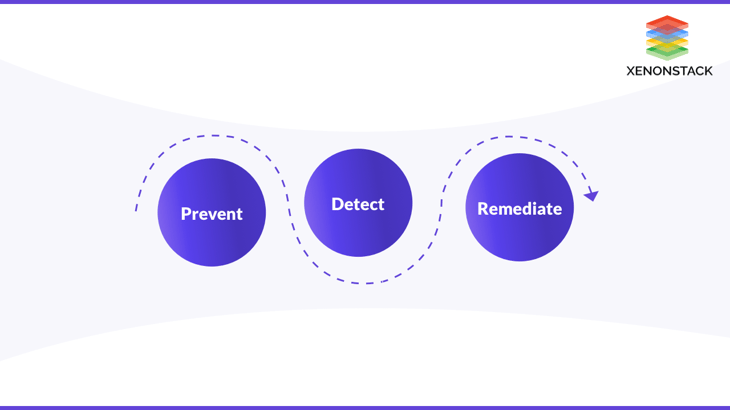
In Simpler terms, compliance as a code can be explained as the codification of the compliance controls to automate their application, remediation, and support. Compliance as a code tool enables compliance by defining how IT resources should be configured to meet the compliance controls. Then these tools are configured to automatically monitor and scan the live environment to detect the non-compliant infrastructure. Compliance as a code enables the three core activities, i.e., Prevent, detect and remediate.
Prevent
Prevent non-compliant issues by automatically making them compliant.
Detect
Detect non-compliant by automatically scanning and notifying the security team whenever any issue is detected.
Remediate
Remediate the non-compliant by making immediate changes to the issues detected in the early stage, and it also ensures the maximum level of compliance at scale.
Implementing Compliance-as-Code from the very beginning of the development lifecycle ensures the timely delivery of a project that tends to be compliant. Click to explore our, Comprehensive Guide to Compliance as Code
Benefits of Automating Compliance
Fast Resolution with Security Checks
Generally, most organizations consider regularly examining security settings as the "secondary priority". Teams usually ignore some checks because it has to be reviewed manually, which is very time-consuming. Continuous compliance transforms the security process into a "primary priority" by maintaining the state of compliance every time, i.e., it is immediately remediated whenever a non-compliance is found. Continuous compliance automates the remediation and monitoring to provide deep visibility into the compliance state of any server.
Reduce human errors and complexity
Before Continuous compliance, everything was done manually, which increases the complexity of the tasks and consumes a lot of time. But with the enforcement of continuous compliance, 100% automation has been made to the things done manually earlier. Hence, it reduces the chances of errors, and also, the complexity has been decreased.
Continuous Monitoring
Continuous monitoring refers to the quality assurance tests that organizations conduct to determine how effectively their operations comply with the regulatory and internal process requirements.
Conclusion
Continuous compliance is a proactive approach that helps to simplify the process of tracking security risks in real-time. Compliance as a code enables compliance by defining how IT resources should be configured to meet the compliance controls. It is hard to keep updated with the changing regulations while ensuring continuous compliance and remediation. Continuous compliance leads to immediate success by eliminating the need to spend countless hours collecting evidence. The detected risks can be mitigated immediately by maintaining a secure security posture.
.webp?width=1921&height=622&name=usecase-banner%20(1).webp)