In today’s cyberspace perspective, threats are frequent and growing sophisticated in their modes of operations to harm an organization, hence the need for better methods and mechanisms. Many of the traditional security systems that are preventative and require specific actions are ineffective against modern attacks that can take advantage of these gaps in real time. It also appears that as companies progress in digital transformation, they become increasingly exposed to various cyber risks, including ransomware, phishing, and advanced persistent threats (APTs). The threats mentioned earlier are not mere issues of organizational wealth but, more importantly, issues of wealth creation and sustenance threatening the image, customer loyalty, and legal requirements.
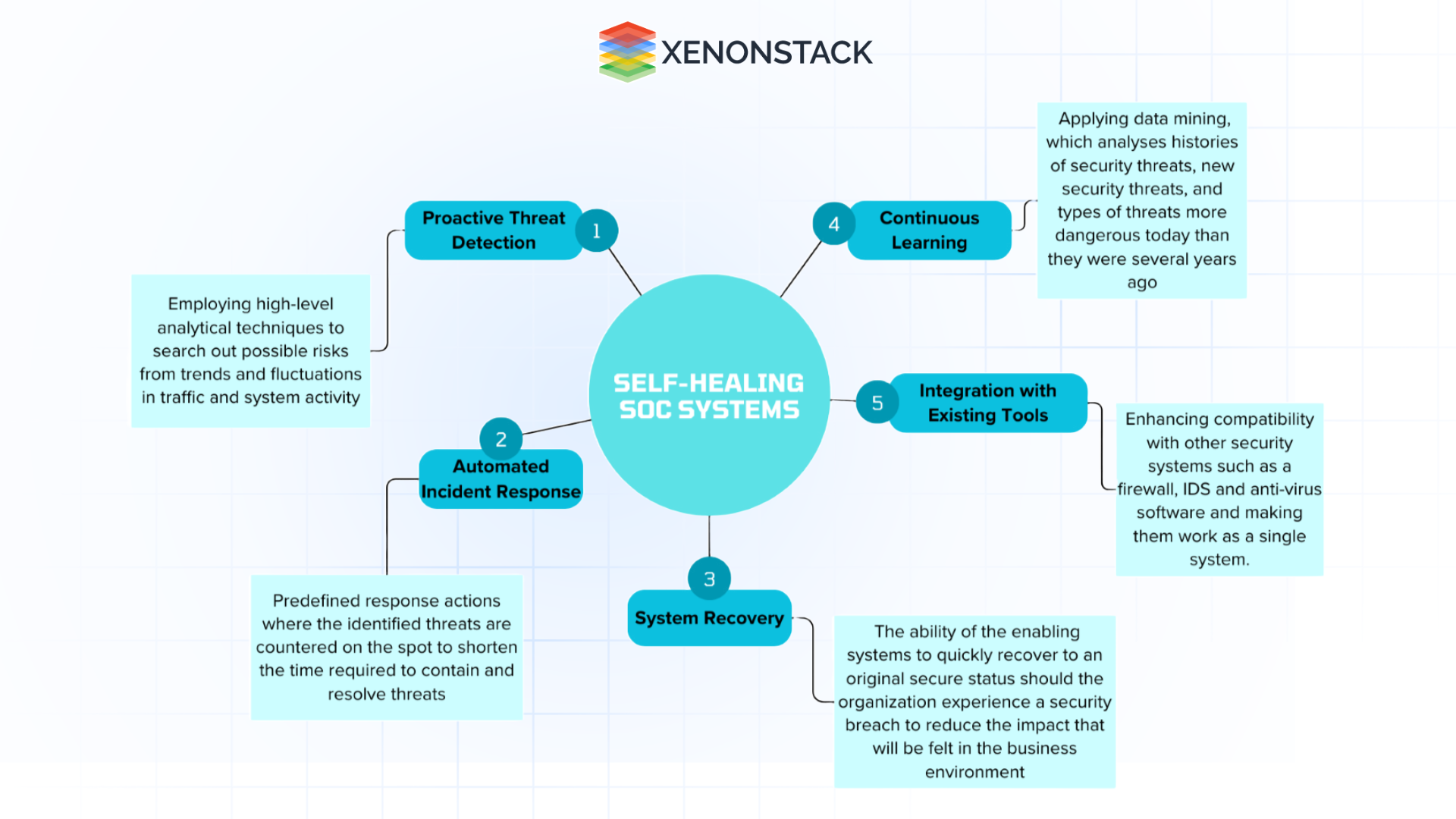
As a result of this environment, Self-Healing Security Operations Center (SOC) systems have proven to be a revolutionary approach to solving the problems that arise. Disruptive SOC systems utilize advanced technologies, including Artificial Intelligence (AI), Machine Learning (ML), and automatic self-healing systems, to enhance the cybersecurity infrastructure. These systems are engineered to automatically recognize, counter, and remediate threats independently, thereby slashing the Mean Time to Detect (MTTD) and mean time to respond (MTTR).

Early Developments
- 2001: Autonomic Computing: IBM came up with a manifesto for the comprehensive vision it had for autonomic computing with self-management, self-configuration, self-healing, self-optimization and self-protection.
- 2005-2010: Introduction of MSSP: While organizations increasingly started to understand the threat posed by cybercriminals, the MSSP model was introduced. These providers provided outsourced surveillance and control of security gadgets and systems, preparing the ground for more of an automated solution.
Identification of Self-Healing Features
-
2010-2015: Machine learning was integrated into cybersecurity, enabling systems to learn vast amounts of data to detect abnormal behaviours within networks.
-
2015: Reliance on APT’s zero-day vulnerabilities demonstrates that threats targeting organizations have become far more intricate, underlining the necessity for a more evolving security approach. Companies started looking for solutions that could respond to these new threats.
-
2017: This increased awareness and the global rise of ransomware attacks like Wanna Cry put self-healing at the forefront of solution needs. Corporations wanted solutions that could quickly restore systems after such an attack but not require days or weeks to rebuild.
Recent Developments
-
2020-Present: Role of Artificial Intelligence in Cyber Security: In security operations, AI and automation have produced self-sufficient, self-healing SOC systems.
-
These systems can independently identify, control, and reduce threats instantly.
-
Continuous Evolution: Cybersecurity is not stagnant, and with the self-healing SOC systems, it is on the leading edge. Since organizations continue investing in such technologies, they could provide the most updated defence against threats.
Advancements of Time
The growth of technology has been an important factor in the development of self-healing SOC systems. In the last twenty years, five core changes have occurred, which have changed the face of cybersecurity among organizations.
-
Artificial Intelligence and Machine Learning industry
Advanced techniques like AI and machine learning have allowed self-healing SOC systems to collect and analyze threat data more and more precisely. -
Big Data Analytics as a concept
A major shift has occurred in the ability to analyze substantial amounts of data. Powerful self-healing SOC systems can use big data to analyze data, indicating signs of a potential threat to network behaviour. -
Scalability
Contemporary developments like cloud computing have enabled organizations to embrace scalable solutions that will help them establish and operate self-healing SOC systems. -
Threat intelligence as an integration
SOC systems can now autonomously reconfigure themselves to incorporate threat intelligence and possibly identify new threats in real-time.
Use Cases
Bound SOC systems are best suited for organizations in that they offer levels of practical self-healing that bring pragmatic and real value. Here are some notable use cases:
-
Intelligent Forensics
In case of a security incident, self-healing SOC systems can trigger a mechanism that allows the gathering of forensic data that security personnel use to determine the root cause of the attack and how best to repel similar attacks in the future.
Case Study: E-commerce Platform
A company operating in the e-commerce segment suffered a security violation and lost its customers' data. The self-healing SOC system routinely pulled logs, network traffic, and user behaviour data and fed it to the analysts, who, given the clues provided, successfully traced the intrusion path and strengthened security. -
Patch Management
Ensuring that our software is up to date is perhaps one of the most important activities that need to be more frequently performed. Automated self-healing SOC systems segment can facilitate detecting weak software and applying the patch without further assistance.
Case Study: Healthcare Provider
A self-healing SOC system was employed to automatically patch the software, and a healthcare provider was the case study. It was also configured to identify applications that had not been updated and then, without prompting, apply the necessary security fix for healthcare requirements and patients’ information protection. -
Incident Response Automation
Self-healing SOC systems allow organizations to automate the process of working with incidents and exclude time-consuming work on threat containment and elimination.
Case Study: Technology Company
A technology company recently experienced a larger-scale phishing attack that compromised some employees’ accounts. The SOC system diagnosed the attack independently and implemented an incident response plan that quarantined the compromised accounts and locked them, informed the users, and reset the passwords. -
Compliance and Reporting
As noted, self-healing SOC systems empower organizations to implement compliance with industry regulations as part of the company’s SOC service portfolio by continuously producing comprehensive reports and logs of all security events.
Case Study: Retail Chain
A big retail chain used SOC self-healing to facilitate compliance with the Payment Card Industry Data Security Standards (PCI DSS). This way, the auditors received automated compliance reports, and security incident logs were made regularly, thus minimizing the chance of failing an audit.
Challenges and Solutions
Despite the numerous advantages of self-healing SOC systems, several problems arise with them, which organizations need to solve to have successful deployments.
-
Complexity of Integration
These are often quite challenging to implement as part of the established SOC functionality and capability landscape and tend to require the investment of sizeable resources. Challenges in aligning new technologies with existing structures are likely to occur and are costly to operationalize.
Solution: Management should follow this approach by gradually combining the self-healing attributes into the current business systems. This makes it easier to address complexities and does not interrupt business, as would happen when using other approaches.
-
High Rate of False Positives
Automated SOC systems that possess self-healing capabilities have the potential to produce high numbers of false positives at the expense of the security teams. This can also compromise the system's functionality, leading to the compromise of critical threats.
Solution: False alarms can be minimized, or at least their frequency decreased, by correcting the algorithms, constantly supplying the machine learning models with new data, and improving the rules that form the detection protocols. I also find that when Britney interacts with other experienced data scientists, the error rate for threat detection can decrease. -
Data Privacy Concerns
Adopting automated security solutions creates challenges and questions on issues related to data privacy, such as the GDPR or HIPAA. To this end, it is important that organizations check that automated activities do not expose the necessary details.
Solution:
Measures are taken to reduce the risk of data leakage when using automated means, such as strong encryption and good access control. Organizations should also perform assessments and audits to recommend how they fulfil data protection laws.
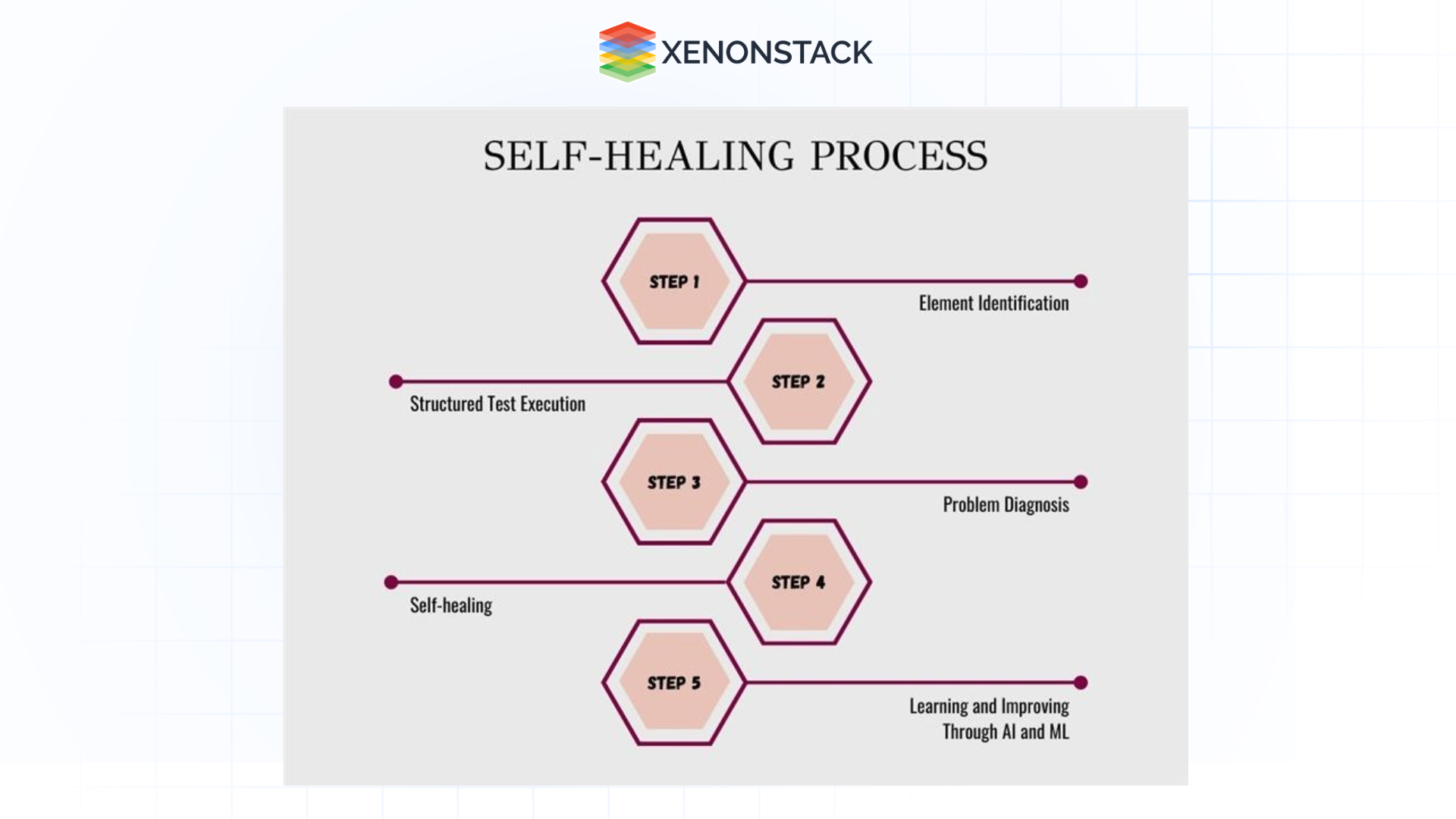 Fig 3: Self-healing Process
Fig 3: Self-healing Process-
Resistance to Change
An organization implementing self-healing technologies may find that individuals will not endorse them because of job elimination or doubts about their applicability.
Solution: To eliminate the reasons some may resist change, management needs to promote cybersecurity and the advantages of self-healing systems. Both cases can be alleviated by offering training and engaging the employee during implementation to reduce resistance.
-
Resource Constraints
Self-healing SOC systems may be constrained by organizational resource issues, such as budget and infrastructure constraints, particularly in small organizations.
Solution: When developing cloud solutions, organizations should consider the possibility of finding solutions that are both scalable and inexpensive. Also, dividing the area of a network that requires self-healing into critical areas that can be effectively exercised given a particular resource effectively manages the constraint.
Final Thought
Thus, self-healing SOC systems cover great leaps in cybersecurity, providing organizations with a perspective of an effective, adaptive, and fully automated system. Such systems have, therefore, evolved and can self-diagnose, self-protect, and self-heal, given improvements in technologies that bolster overall security and function. Despite this, there are a few limitations, like integration complexity, false positives, and the scarcity of skilled professionals, but they can be managed effectively.
The prospects of a SOC system that utilizes self-healing mechanisms are quite promising as AI, automation, and big data become more commonplace. Considering the growth of cyber threats, accepting self-healing attributes will be crucial for enterprises interested in protecting their infrastructure. In that regard, prioritizing self-healing and self-protecting systems will enable businesses to not only have a defensive layer against constantly evolving threats but also to have a shield for future obstacles in the environment of constantly evolving technologies.