Introduction to Video Surveillance for Workplace
The main objective of video surveillance is to protect office assets and valuable information from compromising. For this, there is a need to timely detect and recognize authorized and unauthorized persons, track their activity inside the building so that organizations can identify the situations that require immediate response, which will then require interpretation and action.
The latest AI and production combination promise a stronger, more efficient, and hassle-free working environment in factories. Click to explore about, Cloud Video Analytics and Surveillance for Intelligent Outcomes
Features of Video Surveillance for Workplace
Below are the features which we are considering under our solution:
Process Management with Video Surveillance
In a defined workplace, there are so many different processes, the objective of this feature is to provide the capability to manage the processes using the power of Artificial Intelligence, Computer Vision, and CCTV (which will do the surveillance)
The benefits of process management in Workplace Surveillance are:
- 24*7 process management
- Process management in an automated way without/minimal human intervention.
- In-depth Analysis
Production Analysis with Video Surveillance
Use of AI, Computer Vision, and CCTV to check and analyze production-related issues
The benefits of production analysis with video analytics in workplace surveillance are:
- Analysis of the quantity of production happening during a specific period of time.
- Analyze the peak hour of production
- Analyze the lacking hours of production(which is at its low).
Automated Analytics for Workplace Optimization
Using Analysis and computer vision/ video analysis to optimize the working under the workplace.
The benefits of workplace optimization are:
- Automatic Monitoring of the employees in working hours and its Analysis
Video Surveillance for Behavioral Rules
To track whether every person is following behavioural rules or not
Benefits of surveillance behavioural rules is
- Manage the behaviour of employees without human supervision.
- 24*7 alert on any mishappening
Time Tracking
To track the time/productivity time of the person based on the amount spent on his/her chair or in a specific area
The benefits of time tracking for workplace surveillance:
- When we talk about tracking, it should be 24*7, and it is the benefit here that it can provide 24*7 tracking.
- Not only track time but also ensure the presence of a person in the area(whether he is there or not during the time tracked) where the time is tracked with respect to that person.
According to the Artificial Intelligence Global Surveillance index, at least 75 out of 176 countries globally are actively using AI-based surveillance technologies. Source – How AI Is Making An Impact On The Surveillance World
Activity Monitoring with Video Surveillance
It is very hard to track the activities of employees every minute but using AI and CCTV cameras. It is easily possible to do it and also to generate alerts if any unusual activity is happening.
The benefits of activity monitoring with video analytics are:
- Provide the answer to the following types of questions
- What are employers doing?
- Are they working, or are they wasting time sitting idle?
Crowd Management with Video Surveillance
The objective of this feature is to capability manage the crowd and person under a specific area. It can handle the following questions as to use cases For example:
Benefits of workplace surveillance
- Provide the Analysis of the following questions
- How many people are allowed at a specific place at a specific time?
- How many people are there in a specific place at a particular time?
What are the requirements of workplace surveillance?
The basic requirements of Workplace surveillance is classified in 2 categories.
Technical Requirements
- Python 3.5 or above
- dlib==19.21.1
- face-recognition==1.3.0
- face-recognition-models==0.3.0
Other Requirements
- CCTV cameras access
- Required Employees Data (front, left, and right side of the face)
- CPU-based implementation is very slow. We need a GPU to implement the above scenarios on the CCTV feed.
- Connectivity to Database
Why is a Video Surveillance Dashboard necessary?
Most workplaces remain open 24*7 to serve their customers anytime and provide them value. Therefore employees and visitors always visit there, some for their daily work and some for interviews and consulting. It makes that environment busy, chaotic, un-enjoyable, and unsafe because it may be possible that an unknown person visits with wrong intentions. They can harm the infrastructure as well as the person. Therefore Video surveillance is necessary. One of the organizations’ major challenges is to identify, track and detect those anomalies and persons. Some other challenges of the workplace are:- Identification:
- Paperwork:
- No Anomaly Detection:
- No Historical Tracking:
Video Surveillance Solutions for Businesses
As per the scenarios we are covering, there are two phases to be covered in this solution:
Phase 1: Identification
- Authorized
- Unauthorized
- Temporary Access granted
- Anomaly Detection(Live Tracking)
- Prohibited Area
- Access Control
- Exit
- Map Person
Video Surveillance Solution Phase 1 for Business Case Identification
The solution’s main objective is to develop a model that identifies and classifies the person as authorized and Unauthorised.
Implementation of the solution
- The architecture of the solution
- Steps of the solution
The workflow of the solution is given below in the steps.
Step 1: We should have the images data of authorized persons in this folder
Data →RealTimeImages →Encoding Images →(authorized person images)
Step 2: Detection of faces and recognition of the person’s identity by matching the faces from authorized persons’ saved database. If the person is authorized, it will show a green colour rectangular bounding box around the face of an authorized person; if the person is not permitted, it will show a red colour rectangular bounding box around an unauthorised person.
Step 3: Suppose the person recognises it as unauthorised, then will collect the data of a person.
Step 4: Allocate time-based to enter the building; when the time exceeds, the alert will be sent to the person and authority and track the user if the extra allocated time is still exceeding.
- Output of the solution
From the above approach, we’ll get the following outputs:
|
Output Parameters |
Output Parameters |
Output Parameters |
|
Unique_User_ID |
Access period for Authorized(8hrs, 10hrs, 12hrs, etc.) |
Time Out |
|
Authorized |
Unauthorised(2hrs, 3hrs, 4hrs, etc.) |
Unauthorised purpose(Interview/Official Visit) |
|
Unauthorised |
Date |
Area |
|
Name |
Time In |
Note: The model will generate these columns as output, decided as per the requirement of the AnalyticsOps Team
Usability of Solution
The figure shows how we can use the Identification Feature for Authorisation and
Un-authorization
Phase 2 Solution: Behaviour Analysis and Exit
- This phase of the solution’s main objective is to develop a module that can handle Behaviour Analysis and Exit parts.
- The Camera will map the exit of a user by providing the exit time of the user.
- Implementation of the solution
Step1: Architecture/Steps of the Solution
Step2: Usability of the Solution
Step3: Output of the model
Prohibited Area, Unique_User_ID, Authorized, Unauthorised, Severity, Date, Time, Area, Area wise Duration, Unique_User_ID, Unauthorised(Y/N), Name, Area, Duration, Purpose, date, Entry time, Exit time
Note: The model will generate these columns as output, decided as per the requirement of the AnalyticsOps Team
Overview of the Case Study - Incident
Most workplaces remain open 24*7 to serve their customers anytime and provide them value. Therefore employees and visitors always visit there, some for their daily work and some for interviews and consulting. It makes that environment busy, chaotic, un-enjoyable, and unsafe because it may be possible that an unknown person visits with wrong intentions. They can harm the infrastructure as well as the person. Therefore Workplace surveillance is necessary.Camera-based intelligent video analytics open the minds to widespread possibilities via video streams. Source: Intelligent Video Analytics
Investigation of Video Surveillance
One of the organizations’ significant challenges is to identify, track and detect those anomalies and persons. Some other challenges of workplace surveillance are :
- Identification: Organizations are not able to identify known or unknown people as a lot of people visit the workplace.
- Paperwork: Need a lot of paperwork to handle their entry record. Manual processes are not only inefficient but also increase security risk and costs.
- No Anomaly Detection: Organizations are not able to detect any anomaly at workplaces.
- No Historical Tracking: Organizations are not able to track or map if a person is visiting again and again.
Incident Response
To solve these problems, a solution is necessary that makes workplaces productive and safe using AI and video analytics. The system should detect a person; based on appearance, it recognizes the visitors or regular employees. Then accordingly, monitor access management, behavior analysis, anomaly detection, and alert management to make the system more reliable. It should also analyze the crowd and presence using self-learning analytics. It should also monitor suspicious activities and send an alert to the respective authorities for the actions if encountered. Overall, the system should monitor the whole process using video analytics.How can XenonStack Help?
Xenonstack provides a solution that will cover the following scenario to solve a problem for workplace surveillance :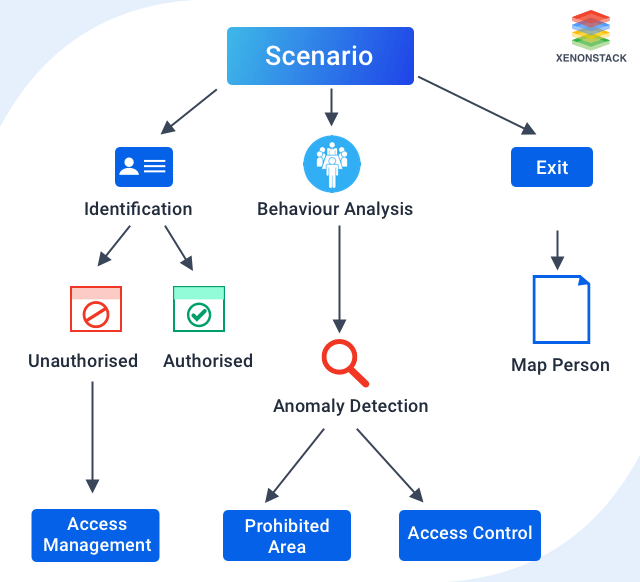 Covering those scenarios, it will allow monitoring the following cases:
Covering those scenarios, it will allow monitoring the following cases:
Boundary Breach Detection
- Virtual Boundary: It allows for tracking the entry and exit of people in a particular area. Thus, users can track the number of visitors, their time of visits, and the duration of their stay there. It allows interlopers to access those areas.
- Forbidden Area Violation: The system generates an alert a person doesn’t have access to a certain area but enters there. It detects real-time violations and malicious activities, thus enhancing the safety and security of the place.
Theft Analysis
- Theft Alert: Systems always track the inventory of a workplace. If it detects any object's movement at an abnormal time, it alerts the manager.
- Loitering: The system keeps track of passers-by and records the time they spend in monitored zones. The system generates an alert when more than usual time is spent by a passerby at the same spot.
Anomaly Detection
- Suspicious Movement Analysis: If anyone spends extra time in a specific location, the system will raise the alarm. Thus detect any suspicious activity before it occurs on-premises.
- Abandoned Object: The system can identify unattended stationary objects, thus detecting threats of cases where objects are left behind with wrong.
- Fire Alert: CCTVs or smoke detectors only detect smoke or fire. But they respond only to smoke or flames after the fire has already begun.
Density/Flow
- Bottleneck Analysis: The system may detect a crowded place immediately and alert the organizer. For taking immediate action to make the environment peaceful by reducing the wait time.
- Entry/Exit Counts: Using a feature-rich camera placed at different locations, users can keep track of the persons and an object entering or exiting the premises.
- Traffic Queueing: The system detects the traffic of people and vehicles at entry gates. And monitor their behavior and early detect the situation before it becomes more cumbersome.
Trip Tracking
- Path Analysis within an Area: The system keeps track of the visitor’s journey to monitor their activity always.
- Presence Distribution Map: Analysing the location and people density in various locations a different times. Users can make decisions regarding scheduling the break and the work timing of people.
Questions to Discuss for Video Surveillance
Still, some questions come in customers' minds: “ How the system will perform”, “How it track a person?”, “When will it generate an alert?”, To answer all these questions, we will discuss a case study for workplace surveillance that will answer all user questions and explain how the system works for an unauthorized person’s journey from entry to exit.- How does the system prevent the entry of unknown people? How does it get to know that a person is unknown?
- Okay, I got to know how the system will detect and prevent the entry of unknown people. But what if a visitor or interviewee comes for the first time? How does the system allow them to come? How does that person get an entry? Whether he/she will be able to come inside the workplace or not?
- As answered in the previous question, that system will give access to them. What is necessary to give access?
- How does the system get to know that the access they were given to is the right person? Because it may be possible that the person is not coming for an interview, he can be the wrong person?
- Okay, As discussed in the previous question, a person will be allowed entry for some defined time. How will the system get to know whether a person leaves at the correct time or not?
- It is also possible that the person that entered the workplace went to the wrong location by mistake or intentionally. Or it may also be possible that person is harming another person or ruining infrastructure. How may the system get to know about that?
- Are these all cases possible for authorized because he/she may also do the same?
- A person may be visiting again and again, but he/she is not a regular person, so he/she has to register themselves? How did the system get to know?
- When does the system stop tracking?
Conclusion
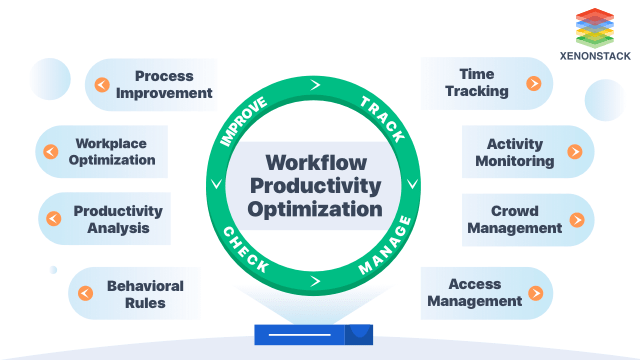
The workplace surveillance solution will track, manage, check and improve employee productivity to keep the workplace safe from theft, sabotage, and malicious activities.
- Discover more about Intelligent Video Analytics for Entertainment Industry
- Click to discover Illegal Parking Detection Using Video Surveillance
- Explore more about Machine Vision Working and Its Applications
- Read more Visual Analytics tools and Processes


