What is your Key focus areas? *
AI Workflow and Operations
Data Management and Operations
AI Governance
Analytics and Insights
Observability
Security Operations
Risk and Compliance
Procurement and Supply Chain
Private Cloud AI
Vision AI
Get Started with your requirements and primary focus, that will help us to make your solution

Agentic Process Automation in Logistics & Supply Chain Management optimizes workflows, improving efficiency and decision-making
28 April 2025
Gain insights on navigating site reliability engineering challenges and best practices for optimizing IT operations and reducing downtime.
03 December 2025
Augmented Intelligence vs Artificial Intelligence in brief details to increase human productivity and future-ready analysis with data-driven ...
14 December 2024

Predictive Analytics tools, techniques, and best practices to predict future outcomes.
29 April 2025

OK Hyperautomation is automation but one level up, it is adding Artificial Intelligence and broader set of tools. Find How it can Change an ...
17 March 2025

ServiceNow AI Agents For Governance, Risk, and Compliance processes to streamline operations and ensure regulatory adherence efficiently
21 November 2025
A Step Guide for implementing the DevSecOps Pipeline in the CI/CD to enhance the Software release workflow with continuous security.
27 October 2024
Explore Scalable edge ai architecture and its benefits, efficiency in processing data locally, reduced latency, enhanced security, and privacy
15 November 2024
Discover how Master Data Management in Supply Chain enhances data accuracy, compliance, and decision-making for improved operational efficiency.
05 December 2024
Explore how to implement Edge AI, optimizing local data processing, enhancing performance, and reducing latency in distributed systems
23 January 2025

Real Time Analytics Tools and Benefits to get real-time insights into gathered data, allowing businesses to make more informed and timely decisions.
13 November 2024

Next-gen Managed Security Services encompassing a holistic approach for Multi Cloud Security, Cyber Security, DDOS protection, Data Protection and ...
02 September 2024
Computer Vision in Supply Chain and logistics industry to increase operational efficiency and safety with real-time insights
28 August 2024

Workplace Analytics an advanced set of data analysis tools and metrics for comprehensive workforce performance measurement and improvement.
01 August 2024

Microsoft Azure Machine Learning Services advantages and its Workflow steps to accelerates and manages the lifecycle of machine learning projects.
17 January 2024

Edge Computing Tools and Applications for on site data processing using Edge devices to ensure data security and data privacy
14 October 2024

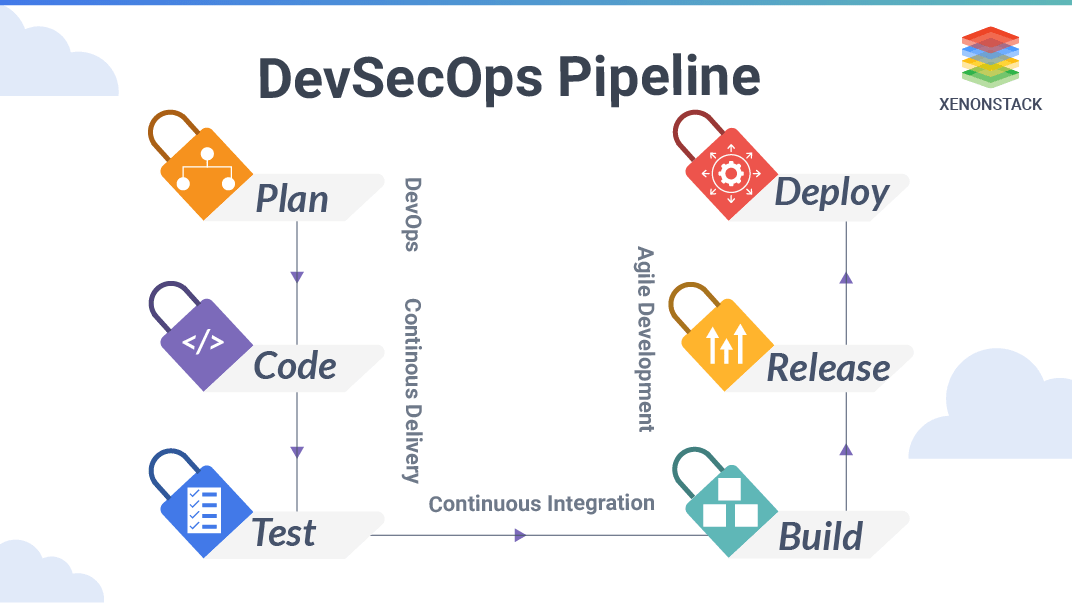
Understand the benefits, architecture, and feasibility of integrating security early in the DevOps environment and adopting DevSecOps
07 March 2025
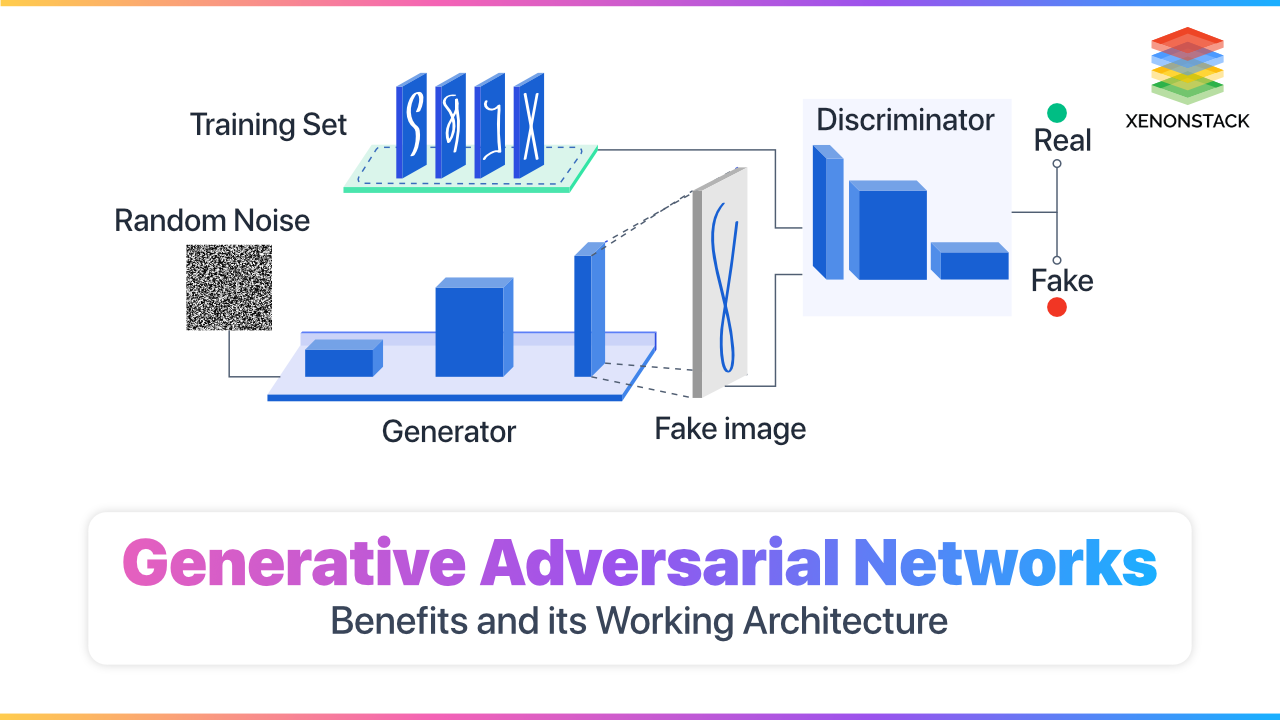
Generative Adversarial Networks Applications, Benefits and its working to generate and receive data samples and do the discrimination between ...
30 August 2024

DevOps best practices include agile project management, continuous deployment, automation, and monitoring
11 December 2024
Transparent AI challenges and approaches for transparency into the inner workings of artificial intelligence systems for decision-making.
01 June 2023
Discover how chatbots boost business efficiency with key benefits, best practices, and implementation strategies for success.
22 January 2025
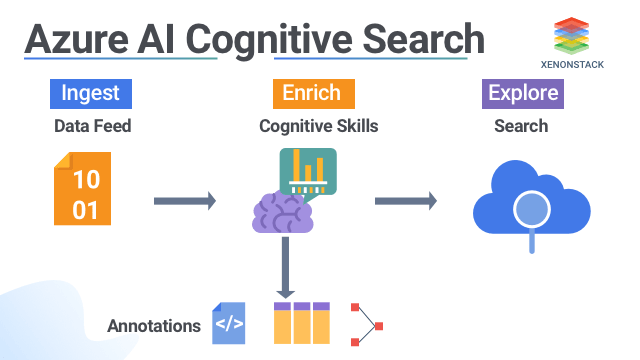
Azure Cognitive Search offers semantic search capability with advanced machine learning techniques to maintain complex cloud search solution.
19 August 2024
Intelligent Process Automation implementation and adoption with best practices along with Artificial Intelligence for speed increment of process.
02 September 2024
Intelligent Robotic Process Automation Architecture, Best Practices for Adopting RPA for Enterprises to Improve processes
06 March 2025

Cloud Security Pillar, Challenges and its Best Practices to protect data, applications, and infrastructure in a cloud computing environment
25 May 2023

Transforming operations with agentic automation for intelligent workflows, real-time decision-making, and scalable AI-driven enterprise processes.
01 May 2025
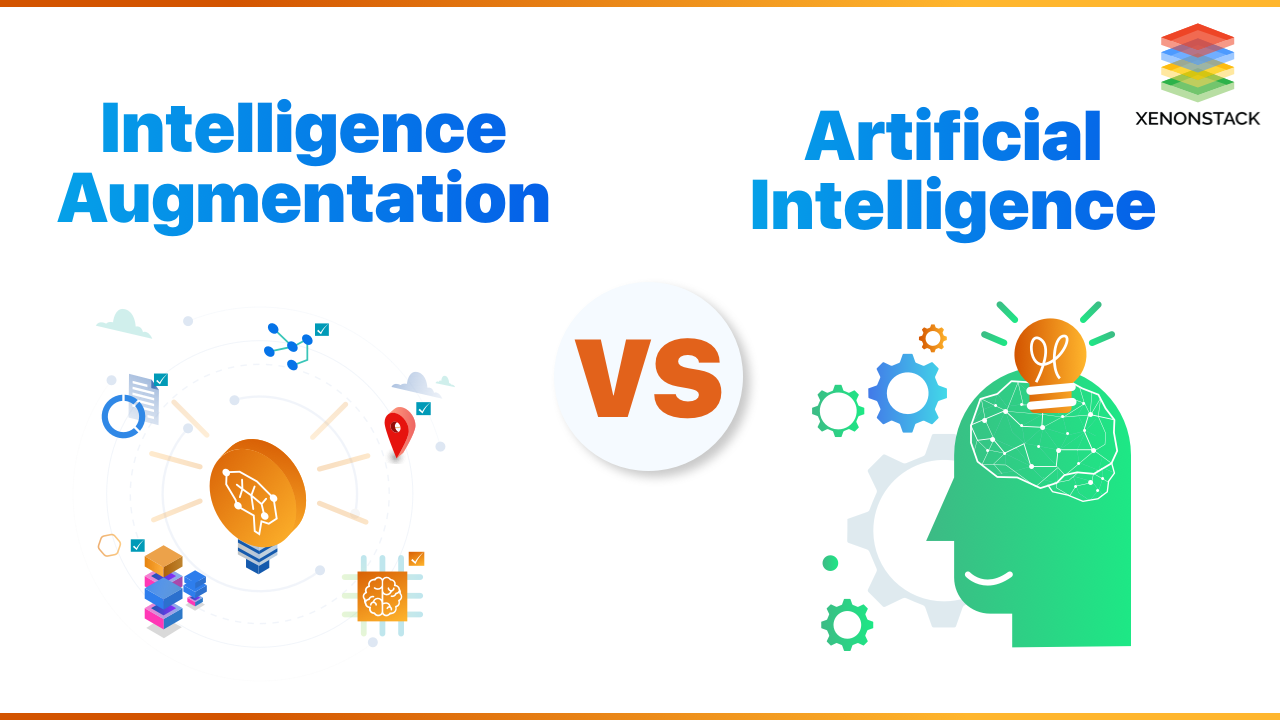
Understanding Augmented Intelligence for real-time Insights and Data-driven Decisions with agentic AI to automate complex tasks and processes
27 October 2024

Continuous Intelligence uses with Artificial Intelligence that enables a company to leverage data in real time for business operations and ...
02 September 2024
Applications of Edge Computing with their industrial benefits in various sectors for faster insights, business benefits, and reduced response time.
23 April 2025

Multi Access Edge Computing (MEC) is the ongoing rollout of 5G networks that are utilizing mobile edge computing for ultra-low-latency needs.
14 August 2024
Cloud Data Warehouse can become a competitive advantage. Learn how to establish a cloud data warehouse with best Practices, benefits, use cases and ...
06 November 2024
Internet of Things Working, Tools and Use Cases for Enterprises to Operate in Network with connected devices to gather and share data using sensors.
25 April 2023

Find out how the key elements of an effective RPA implementation strategy can enhance your organization’s efficiency and responsiveness.
06 December 2024

Learn key strategies for scaling Agentic Process Automation, enhancing performance and automating complex processes seamlessly.
28 April 2025
An incredible roadmap by google to hyper-automate the organizational repetitive tasks, its features, and best practices with UiPath, Blue Prism.
02 September 2024

Successful Agentic Process Automation implementation streamlines workflows, enhances decision-making, and boosts operational efficiency across ...
28 April 2025

Business Process Automation Tools to empower the end-to-end business processes management for higher team member engagement, and improved customer ...
02 September 2024

RPA in Productivity Paradox enhances the results of organizations for business growth and development and increases customer satisfaction.
02 September 2024

Responsible Metaverse Characteristics and its use cases to have a digital version of our real-life with every surreal possibility ever imagined.
10 April 2023
AI in Telecom industry Use Cases, advantages and applications of Artificial Intelligence in Telecom sector to raise quality of networking applications
23 December 2024

Auto Indexing with Machine Learning Working Architecture, Tools and Best Practices for Adopting Automated Indexing with ML
15 November 2024
ModelOps tools, lifecycle and operations for every organization's enterprise AI approach to converge multiple AI objects, solutions, and frameworks
22 October 2024

Complete Guide to Machine Learning Observability and Monitoring of ML Models in Production via both Operational Data Science Perspectives.
27 March 2023

AI Governance Strategy and Best Practices to evaluate and monitor the Artificial Intelligence models to drive business growth.
27 March 2023
The rise of Artificial Intelligence (AI) in Enterprise did many things, especially in data-driven enterprises to interpret business processes across ...
10 September 2024
Complete Overview of AI Adoption Principles, Challenges and its Modern Solution for Business Growth and Development.
10 September 2024

Discover how Agentic Process Automation in Travel and Hospitality enhances efficiency, personalization, and customer experience.
28 April 2025
SAP Intelligent Robotic Process Automation (SAP Intelligent RPA) is an automation solution that allows both skilled and inexperienced developers to ...
02 September 2024
Apache Storm security in conjunction with Apache Kerberos best practices, design, and functionality, enables businesses to process data securely.
16 March 2023

AWS Security Tools, Configuration and its use cases to check the configuration of the resources and records valuable information.
16 March 2023

Application security Checklist and strategy to consider in 2023 for securing applications against emerging cyber attacks in evolving threat landscape.
15 March 2023

Discover how Agentic Process Automation for Robust Cybersecurity strengthens protection, improves operational efficiency, and accelerates threat ...
28 April 2025
Supply Chain Security best practices to help enterprises to detect and remediate vulnerabilities throughout the software development lifecycle.
06 February 2024

Cybersecurity Framework and best practices for businesses to manage risks and reduce exposure to vulnerabilities that cyber criminals may exploit.
14 March 2023

Application security best practices to keep enterprises on top of security for minimizing the risk of data and code breaches.
10 September 2024

Vault Kubernetes is ideal for Secret Management in Kubernetes and offers critical services in the fields of Identity Management, and Compliance.
23 September 2024
Multicloud ModelOps enable enterprises to optimize their data science and AI investments with data, models and resources from edge to core to cloud.
22 October 2024

Digital identity is the key for enabling Web 3.0 to interact securely and provide privacy, control, openness, and interoperability.
02 July 2024
Understanding Cyber-Physical Systems (CPS) and Their Elements explores the key components and applications driving innovation in technology.
21 November 2024

Overview of kafka and zookeeper architecture to solve the low-latency ingestion of large amounts of event data.
10 October 2024
Complete Overview of Deep Learning application with its challenges and solutions for various industries adopting Generative AI.
28 August 2024

Scaling and Governing your Enterprise AI initiatives with ModelOps to deliver business value from the deployed ML model.
12 August 2024
Automation in manufacturing industry with Robotic Process Automation (RPA) to automate repetitive tasks, reduce error rates and increase productivity.
06 February 2024

Cognitive Analytics Tools and Architecture to apply intelligent technologies in changing society and Improving Productivity and Efficiency.
24 November 2023
Industry 4.0 Digital Twin technology and its smart manufacturing applications enhance efficiency, predictive maintenance, and real-time optimization.
21 April 2025

Metaverse Continuum for the connectivity of social media with the unique affordances of VR and AR immersive technology.
05 January 2023

Learn how cloud monitoring tools optimize performance, providing real-time insights, cost management, security, and scalability for businesses.
10 January 2025
Explore quick guide for anomaly detection in cybersecurity networks. Learn how spotting unusual behavior can fortify security and prevent cyber ...
15 November 2024
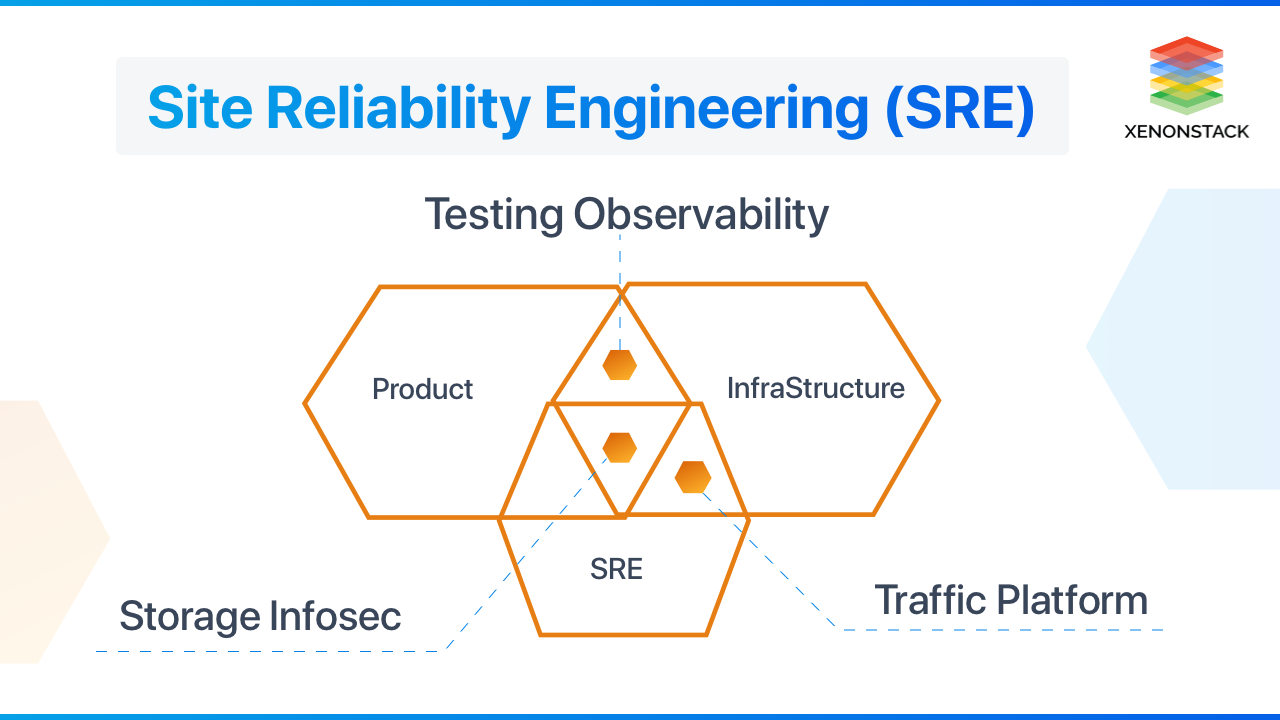
Site Reliability Engineering (SRE) bridges gap between development and operations team. Get to know its benefits, principles, and much more.
29 October 2022

Geospatial Visualization Tools and Techniques to visualize large geographically related data for better navigation and geographical locations with ...
01 September 2022
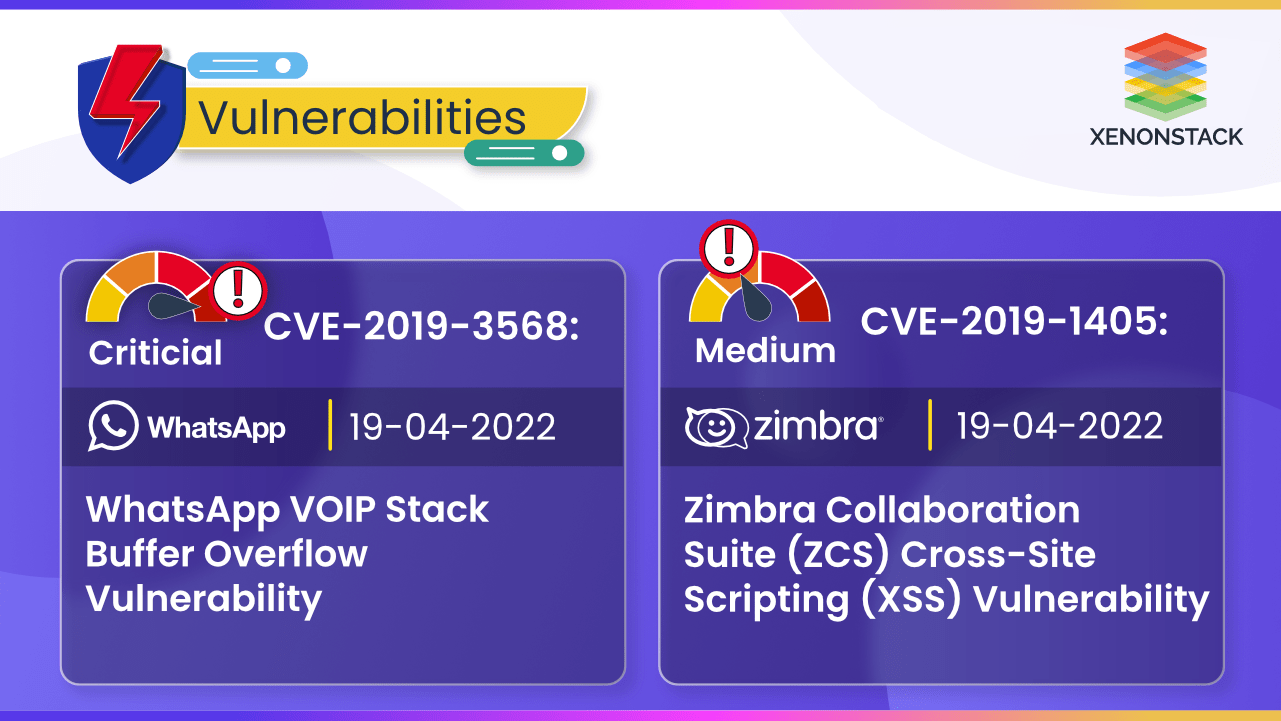
CVE-2019-3568 (Whatsapp) and CVE-2018-6882 (Zimbra) Vulnerabilities allow attackers to remotely inject arbitrary HTML or remotely execute code
16 December 2022
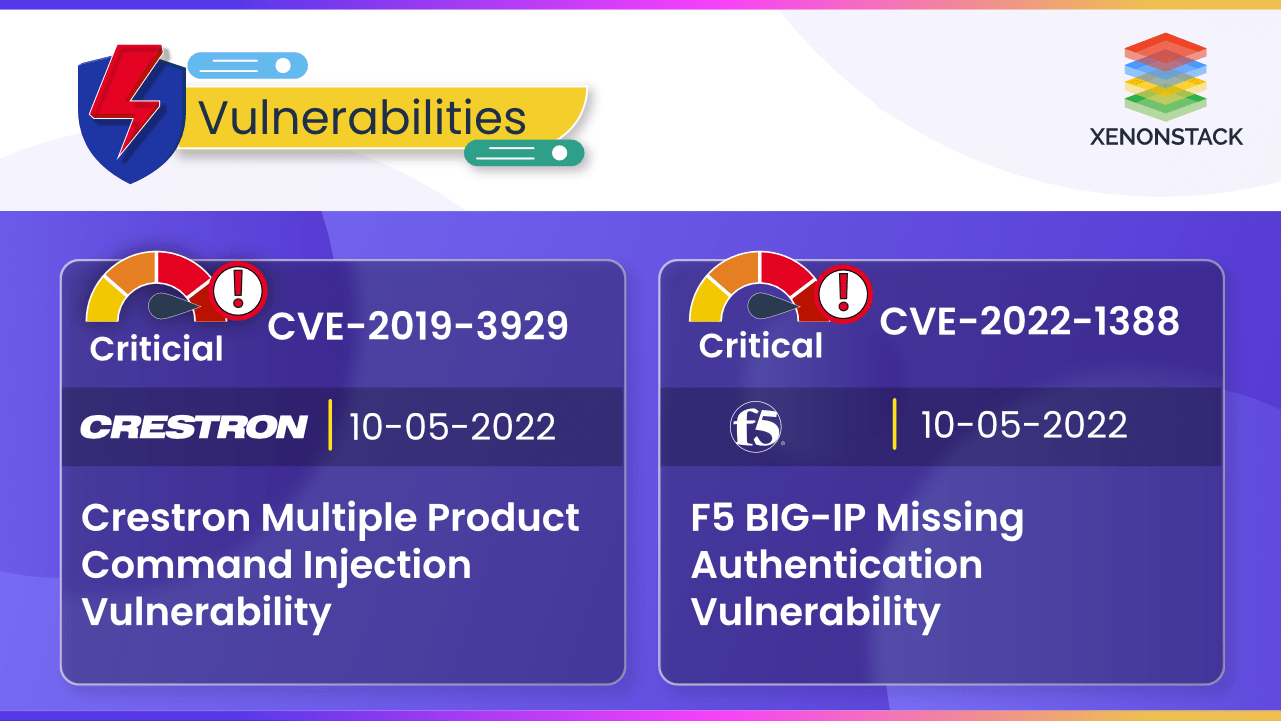
CVE-2019-3929 and F5 CVE-2022-1388 vulnerabilities can leads to priveledges escalation and remote code execution
16 December 2022
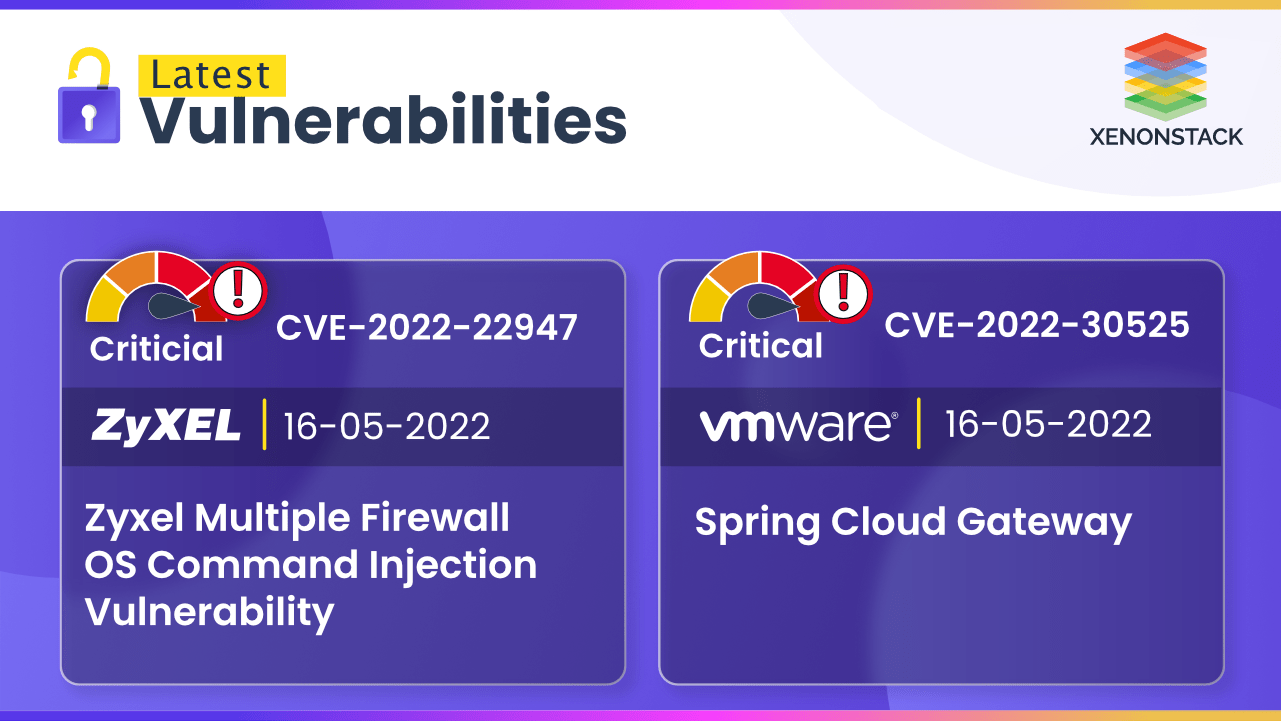
CVE-2022-22947 and CVE-2022-30525 are Code and Command Injection Vulnerabilities that can allow an attacker to modify files and execute OS commands.
10 September 2024
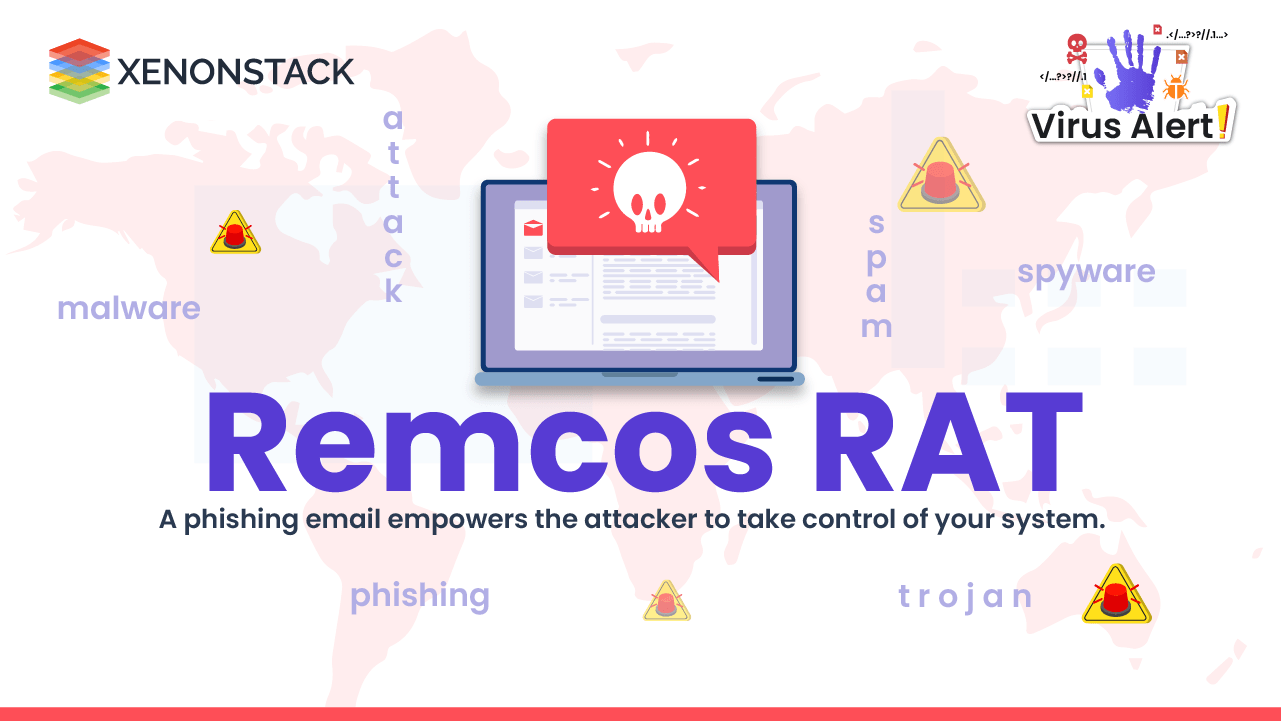
Remcos RAT malware targeting Windows-based computers gives the attacker complete remote control over the systems via phishing email to steal user ...
20 August 2022
CodeRed Worm propagates through networks, uses a vulnerability in Microsoft's IIS, and launches a DoS attack to suspend all activities.
20 August 2022

Unified Identity and Access Governance Solution can help Enterprises in limiting the access request to users for streamlining operations
30 August 2024

SecDevOps employs continuous and automated security testing even before the application is deployed, It ingrains culture of a security-first firm ...
10 September 2024
Cloud Security is a set of policies, procedures, and controls that together protects Cloud-Based Applications, data, and Infrastructure.
29 April 2025
The Sasser virus finds a vulnerable system, copies itself into the Windows system directory, and is launched the next time the computer is booted.
20 August 2022

Spring4shell (CVE-2022-22965) is a vulnerability in the Spring Java framework that execute code remotely and compromises a huge number of servers
22 August 2022

Clop Virus belongs to the Cryptomix ransomware family which actively avoids unprotected systems and encrypts saved files by planting the Clop ...
22 August 2022

Tinba is a tiny banker trojan that uses a spoofed website of a financial institution to redirect sensitive information, login credentials to the ...
30 August 2024
Delta Electronics DIAEnergie (CVE-2022-25880) and Sophos Firewall (CVE-2022-1040) Vulnerabilities allows remote code execution
16 December 2022
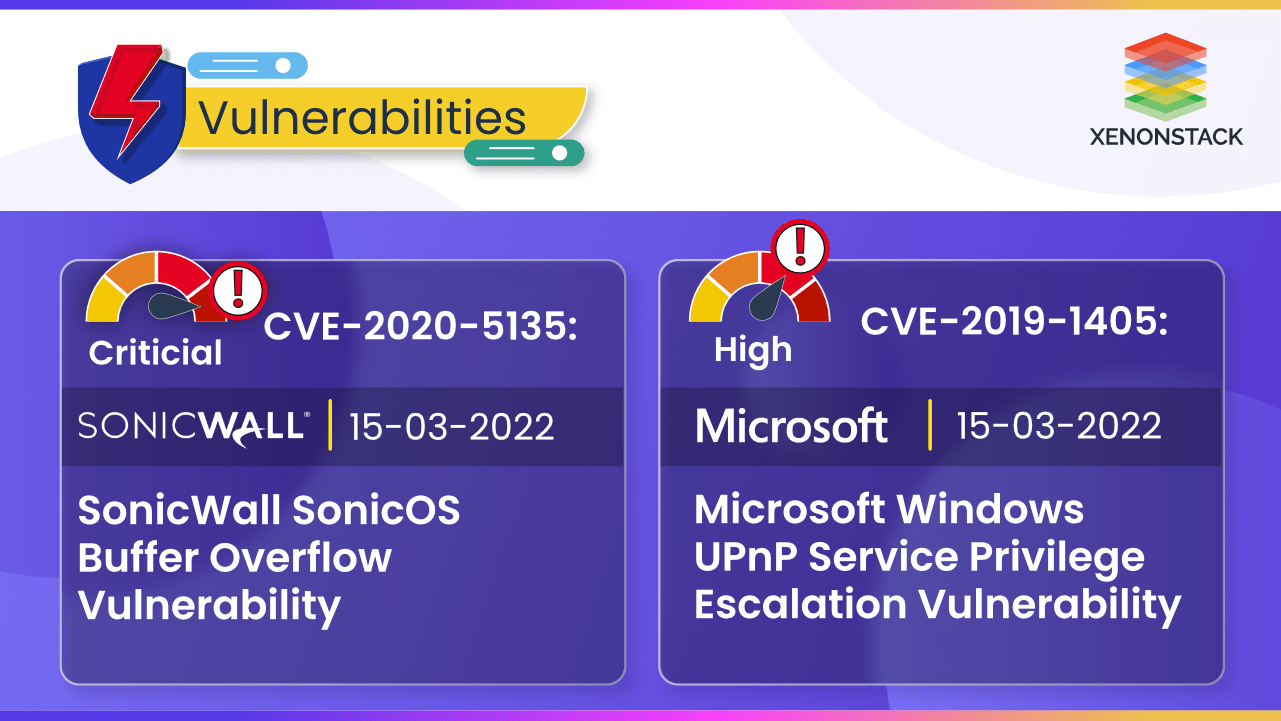
SonicWall's CVE-2020-5135 and Microsoft's CVE-2019-1405 vulnerabilities can cause disruption in the availability of resources
16 December 2022
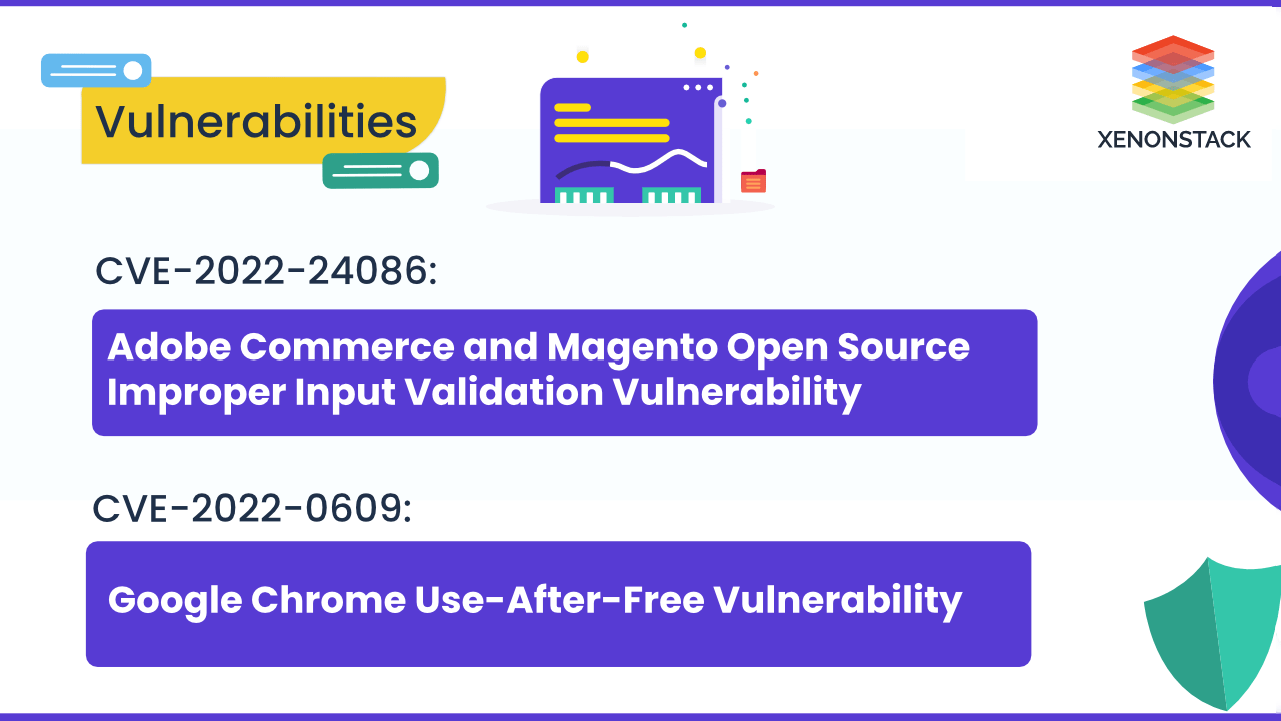
CVE-2022-24086 Vulnerability in Adobe Commerce and Magento Open Source and CVE-2022-0609 Vulnerability in Google Chrome allows arbitrary code ...
30 August 2024

Zimbra Webmail Cross-Site Scripting (CVE-2022-24682) and Microsoft Office Remote Code Execution (CVE-2017-8570) vulnerabilities allow access to the ...
30 August 2024
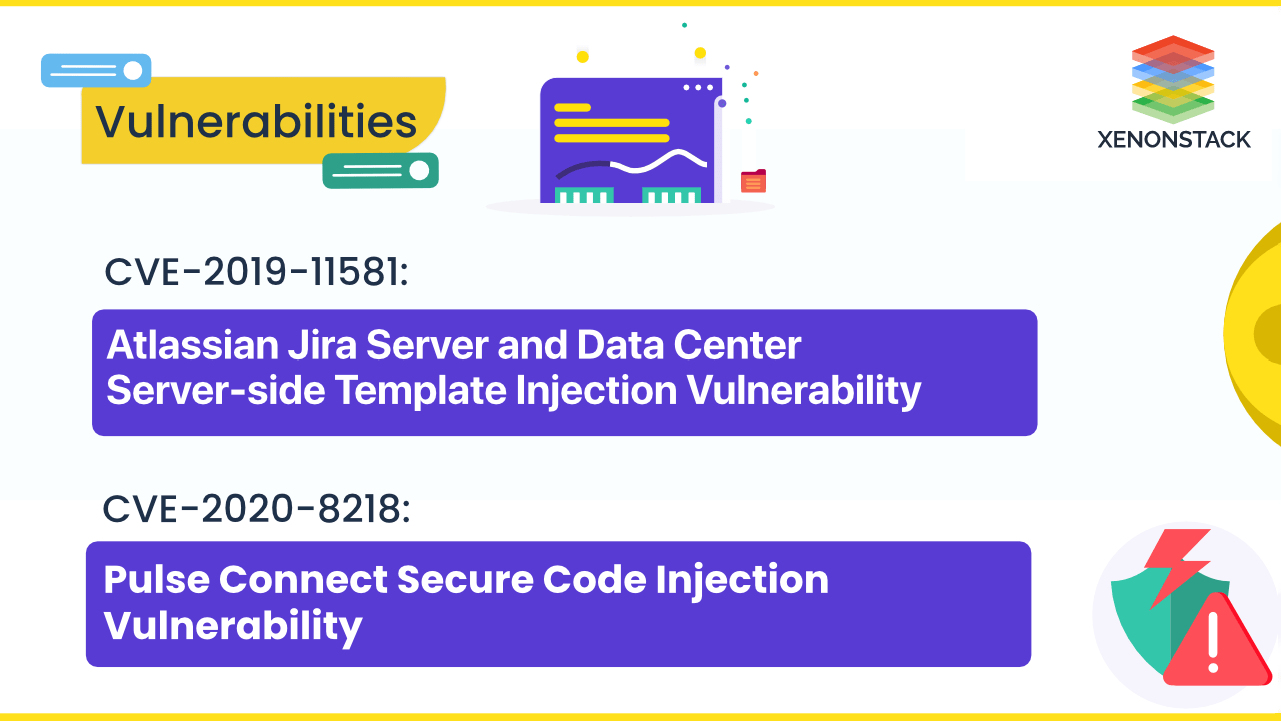
Atlassian Jira CVE-2019-11581 and Pulse Connect CVE-2020-8218 Injection Vulnerabilities allow attackers to execute arbitrary code
16 December 2022

The VMware CVE-2021-21973 (SSRF) and NETGEAR CVE-2017-6077 (Remote Code Execution) Vulnerabilities have the potential to compromise your entire ...
16 December 2022
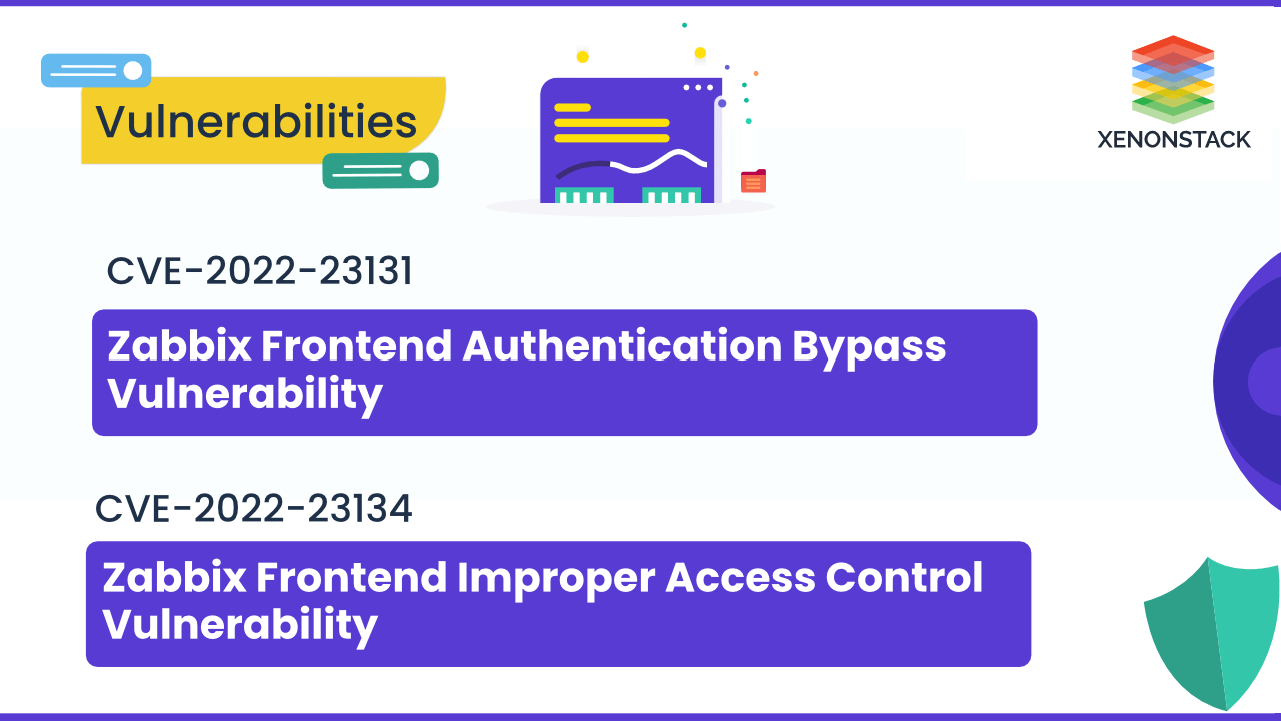
CVE-2022-23131 and CVE-2022-23134 Vulnerability in Zabbix Frontend could result in frontend settings alteration and Authentication instances takeover
16 December 2022

Learning Analytics Platform and models helps to predict learners’ performance, personalized eLearning experience. Explore best Learning Tools.
08 August 2022

Agentic Process Automation in Telecom optimizes workflows, enhances operational efficiency, and drives intelligent, real-time decision-making.
28 April 2025

Explore effective Agentic Process Automation testing strategies to optimize efficiency, improve accuracy, and enhance automation outcomes.
28 April 2025

HIPAA Compliance checklist, security rules and Privacy for the protection of patient information with the increase in electronic medical records
25 June 2024
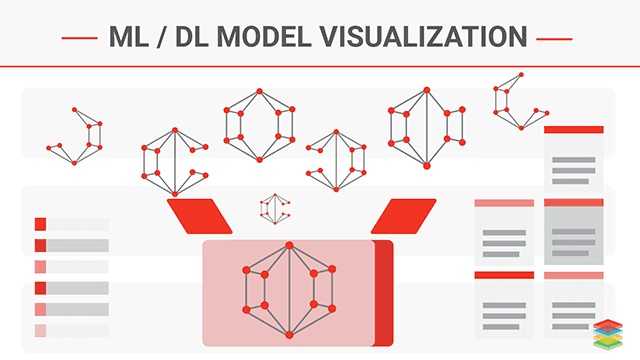
Machine Learning and Deep learning Model Visualization and Neural Network for Model Prediction, accountability and transparency on the model.
30 August 2024

Capsule Networks benefits, Best Practices and its working architecture to pass the information of the lower-level neurons to higher level neurons.
16 March 2022

Apache HBase Security Architecture and its component to secure HBase with Kerberos and create a protected service session.
11 March 2022

AIOps for telecom industry enhance operational efficiency, automate processes, improve incident management through intelligent insights and data ...
03 October 2024
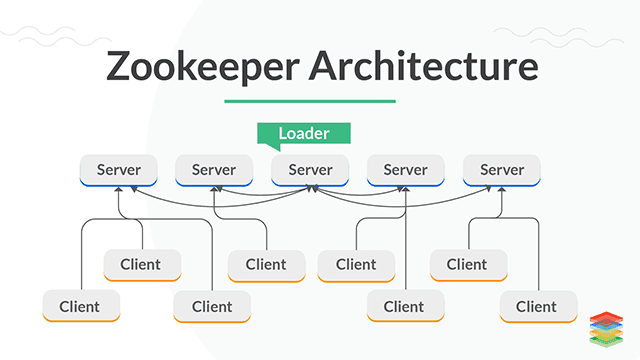
Apache ZooKeeper Security, Architecture, and its Installation on AWS EC2 Instance for managing large hosts, maintenance and configuring information.
09 March 2022
Enterprise Machine Learning Guide to transform your corporate model to accelerate activities on a large scale and new business opportunities.
10 September 2024

Machine Learning Model testing tools, training, Monitoring test sets and importance of cross validation in ML and Deep Learning
27 February 2024
Understanding Botnets and how does it work, best Anti-Botnet Tools and Best Practices to protect endpoint devices and malware unbeknownst to users.
28 February 2025

Build a personalized contact center with Amazon Connect using Agent Assist for real-time insights, automation, and omnichannel support.
09 April 2025

Compositional AI for developing a new combined module by using existing or new different sub-modules which will perform a specific part of the ...
28 November 2023

Discover how Agentic Process Automation Governance enhances RPA, driving intelligent automation, security, scalability, and real-time optimization.
28 April 2025

Leveraging Text Analytics for enhanced Customer Experience to unlock the potential of unstructured data and transfer it into commercial value for ...
21 April 2022

A starter guide to Anomaly Detection with Deep Learning. This blog covers the Anomaly Detection Techniques, Use-cases and more.
18 April 2022

Get to know how MDM Manufacturing data management processes have helped and aided the manufacturing sector and transformed it in a whole.
06 February 2024
AI continuously monitors systems for risks before they escalate. It correlates signals across logs, metrics, and traces. This ensures faster detection, fewer incidents, and stronger reliability
AI converts camera feeds into instant situational awareness. It detects unusual motion and unsafe behavior in real time. Long hours of video become searchable and summarized instantly
Your data stack becomes intelligent and conversational. Agents surface insights, detect anomalies, and explain trends. Move from dashboards to autonomous, always-on analytics
Agents identify recurring failures and performance issues. They trigger workflows that resolve common problems automatically. Your infrastructure evolves into a self-healing environment
AI continuously checks controls and compliance posture. It detects misconfigurations and risks before they escalate. Evidence collection becomes automatic and audit-ready
Financial and procurement workflows become proactive and insight-driven. Agents monitor spend, vendors, and contracts in real time. Approvals and sourcing decisions become faster and smarter