Zimbra Webmail Cross-Site Scripting Vulnerability (CVE-2022-24682)
What is CVE-2022-24682?
Synacor Zimbra Collaboration Suite up to 8.8.15 Patch 29 (Groupware Software) was found with a critical vulnerability. This problem affects an unidentified part of the Element Attribute Handler component. A privilege escalation vulnerability is created by manipulating an unknown input. CWE-74 is the result of using CWE to declare the problem. Confidentiality, integrity, and availability are all impacted.
In a sequence of spear-phishing email attacks, the system known as TEMP_Heretic was exploited. The threat actor will first conduct reconnaissance, using tracker-embedded emails to determine whether an address is accurate and whether a target would even open emails in the first place — if so, the second stage of the assault chain will begin. The initial emails were sent from 74 different Microsoft Outlook email addresses and contained generic graphics and themes such as invitations, alerts, and airline ticket refunds.
The exploit would require the victim to be logged into the Zimbra webmail client via a web browser when they opened the malicious attachment & link. Still, Volexity claims that the link could be launched from other apps like Outlook or Thunderbird.
The XSS vulnerability allows attackers to run arbitrary JavaScript in the context of a Zimbra session, allowing them to steal message contents, attachments, and cookies.
In addition, fraudsters might utilize a hijacked email account to send subsequent phishing emails or create prompts for the victim to download other malware payloads.
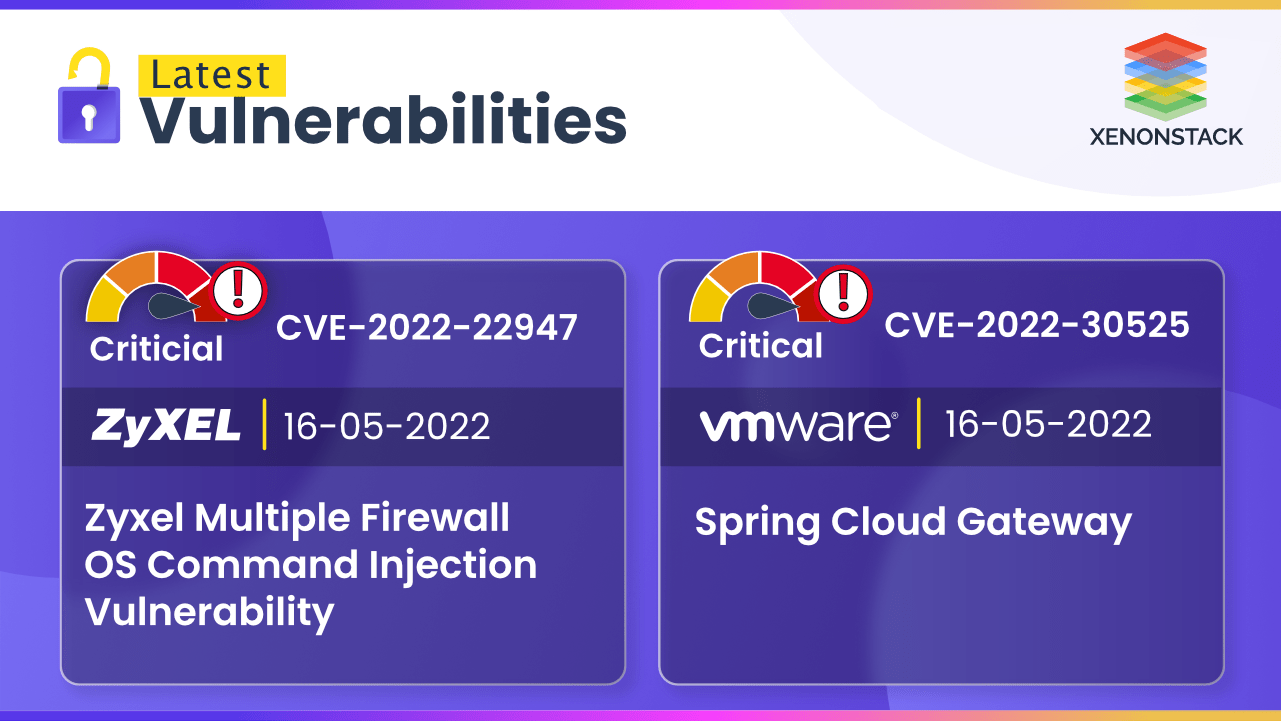
| CVE ID | CVE-2022-24682 |
| Vulnerability | Zimbra Webmail Cross-Site Scripting Vulnerability |
| Vendor | Zimbra |
| Product | Webmail |
| Date added to the catalog | 2022-02-25 |
| Severity (Scale out of 10) | 6.1 (Medium) |
| Description | OS command execution via a crafted POST request to multiple admin APIs affects Accellion FTA 9_12_370 and earlier. |
Impact of CVE-2022-24682
The attackers might also steal cookies and acquire continued access to mailboxes, send more phishing messages to victims' contacts, and trick targets into installing malware by accident.
| Vulnerability | Remediation |
| Zimbra Webmail Cross-Site Scripting Vulnerability | This issue can be resolved by installing patch 9.0.0 as it is unaffected by the vulnerability. |
Microsoft Office Remote Code Execution Vulnerability (CVE-2017-8570)
What is CVE-2017-8570?
The way Microsoft Office manages objects in memory allows for a remote code execution vulnerability, sometimes known as the "Microsoft Office Remote Code Execution Vulnerability."
CVE-2017-0243 is not the same as this CVE ID. Some malicious RTF documents are used as malspam attachments to exploit the vulnerability to install malicious payloads on victims' machines.
A user must open the file with an affected version of Microsoft Office software to exploit the vulnerability. In an email attack, an attacker might take advantage of the vulnerability by emailing the victim a specially crafted file and convincing them to open it. An attacker could host a website (or utilize a compromised website that accepts or hosts user-provided content) containing a crafted file tailored to exploit the vulnerability in a web-based attack scenario. On the other hand, an attacker would have no method of forcing the user to visit the page. Social engineering techniques such as bogus product order requests and invoice documents are used in these spam and phishing emails to persuade victims to click the files. Currently, this flaw acts as a downloader for other well-known viruses like Loki and Nanocore.
| CVE ID | CVE-2017-8570 |
| Vulnerability | Microsoft Office Remote Code Execution Vulnerability |
| Vendor | Microsoft |
| Product | Office |
| Date added to the catalog | 2022-02-25 |
| Severity (Scale out of 10) | 7.8 (High) |
| Short Description | A remote code execution vulnerability arises when a Microsoft Office application fails to handle objects in memory properly. |
Impact of CVE-2022-23134
Compromise system security - downloads and installs additional malware.
Currently, this vulnerability acts as a downloader for other well-known viruses like Loki and Nanocore.
| Vulnerability | Remediation |
| Microsoft Office Remote Code Execution Vulnerability | Use the latest updated |