Introduction to Cybersecurity Framework
In our day-to-day life, we witness numerous cases of cyber attacks, money frauds, cyber crimes, and various other incidents related to litigation of cyber security. Government and security agencies issue various statistics that predict that cybercrime is increasing at a high rate. These cyber-attacks may vary from mild level to advanced level. In today’s world, almost all organizations are reliable on the Internet for their work. So it becomes a major concern to develop a Unified Cyber Security Monitoring and Management Framework. Some of the advanced cyber-attacks are :- Swiper (Flame)
- Stuxnet
- Zeus Botnet
Companies need to embrace and adopt automation, big data solutions, and artificial intelligence to cope with the ever-increasing number of alerts and incidents Source: Perspectives on transforming cybersecurity
What are the Cybersecurity Challenges?
Ransomware Evolution: According to the statistics published by Sophos, more than 80 percent of Indian companies became Ransomware victims. Ransomware attacks are the ones that prevent users from accessing their data until the demanded amount is paid. AI Expansion: Through AI and machine learning, technologies provide us with many benefits, and they also come with drawbacks. IoT Threats: Cybersecurity challenges are increasing with the increase of IoT devices. Protection of these IoT devices has become the biggest challenge in Cyber Security. So to overcome these challenges, we need a framework that will help us to enhance our security.What is the Cybersecurity Framework?
The cybersecurity framework is a series of documents that defines the best practices that an organization needs to follow to tackle cybersecurity challenges. Such frameworks help reduce the industry’s exposure to vulnerabilities.What are the types of Cybersecurity Framework?
The most frequently used Cyber Security frameworks are:
PCI DSS (Payment Card Industry Data Security Standard)
This framework comprises a set of security controls implemented to protect payment account security. It is designed to provide protection for credit card, debit card, and cash card transactions.
CIS (Critical Security Controls)
It is a specified arrangement of activities for cyber protection that gives approaches to stop today’s most prevalent and dangerous attacks. The main advantage of these Controls is that they focus on a small number of actions with high results and outcomes.
NIST Framework
This framework helps improve an organization’s critical infrastructure Cybersecurity to enhance a company’s willingness to manage cybersecurity risk by leveraging standard methodologies and processes.
All tech giants are trying to develop cutting-edge AI technology to have a major impact on humanity’s development. Source: Ethical AI Challenges and it’s Solutions
What are the Components of Cybersecurity Framework?
- Framework Core: The framework core contains guidance information that defines industry standards in such a way that will help industries tackle cyber risks.
- Implementation Tiers: Tiers serve as a method for the organization to evaluate its current cybersecurity posture. They help organizations to calculate the degree of standards that are best for their cybersecurity program.
- Profiles: It helps companies create a blueprint that will minimize the cyber risks oriented with the company’s goals. Companies may concentrate on more than one profile to detect weak spots and opportunities for improving the cybersecurity posture.
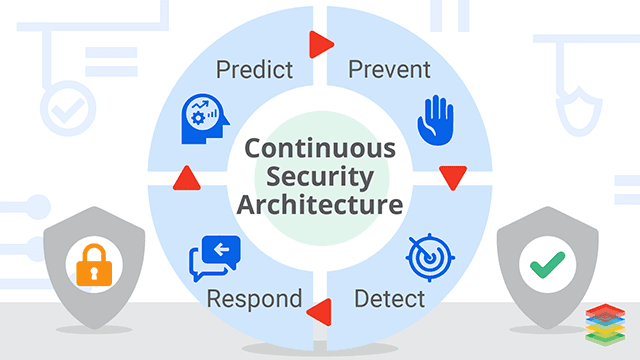
What are the Functions of Cybersecurity Framework?
The most frequently used Cyber Security functions are:Identify
The Cyber Security Framework requires organizations to recognize their environment completely in order to manage cybersecurity risks at the data, asset, and systems levels. This is the point where we calculate the conditions of our industry. To follow or obey this aspect of the framework, organizations need to identify their assets completely,Protect
This function aims to determine how the current cybersecurity policies are protecting our organization and where they are lacking.Detect
This function includes continuous monitoring to identify any unusual activity or any other risks. So basically, the role of detect function is to quickly detect any anomalies.Respond
The “Respond” function covers all the required activities for a person to take steps after a cybersecurity incident or accident is detected. To do this, the organization must create a detailed response plan and analyze the effectiveness of response following actual cybersecurity events. The five categories surrounded in this function are:- Response Planning
- Communications
- Analysis
- Mitigation
- Improvements
Recover
The “Recover” function helps restore capabilities and services that were damaged as a result of a cybersecurity attack. This function helps in recovering data that was lost, restoring capacities that were damaged, and ensuring that everything is functioning as planned.
The process of protecting the networks, computer systems, and programs from any cyber or digital attacks. Click to explore about, The Ultimate Cyber Security Checklist
how to Implement Cybersecurity Framework?
Described below are the Steps to use Cyber Security Framework are:
Prioritize and Scope
- Identify business objectives
- Describe cybersecurity risks
- Identify organizational components to use Framework.
Orient
- Identify the assets, systems, requirements, and risk management approaches.
- Determine how to evaluate the current risk management and cybersecurity posture.
Create a Current Profile
- Map current cybersecurity and risk management practices to a framework implementation tier.
Conduct a Risk Assessment
- Identify cybersecurity risks
- Evaluate and analyze risks
- Identify risks above tolerances
Create a Target Profile
- Describes desired cybersecurity outcomes
- Account for unique risks
- Develop target profile
- Develop target implementation tier.
Determine, Analyze and Prioritize Gaps
- Compare the current profile and target profile
- Determine the resources to address gaps and create a prioritized action plan.
Implement Action Plan
- Implement necessary actions.
- Monitor cybersecurity practices against the target profile.

Conclusion
Data is one of the most important virtues. Organizations should take steps to secure this data by adopting a comprehensive cybersecurity framework. These Cyber Security frameworks, if properly implemented, can help our organization to deal with various cyber incidents. Data security should be our topmost priority as each, and every activity in our day-to-day life includes the use of data. If we want to secure our confidential data from cyber thieves, we must use a framework in our day-to-day operations.
- Read more about Anomaly Detection for Cyber Network Security
- Click to explore Robotic Process Automation in Cybersecurity