Overview of AI in Cybersecurity
Current Technologies put the organization's cyber security at risk. Even with the advancements in new security strategies, security professionals sometimes fail. Combining the strength of Artificial Intelligence in cyber security with the skills of security professionals from vulnerability checks to defence becomes very effective. Organizations get instant insights and, in turn, get reduced response time. The type of attacks we are prone to currently are -Advanced Malware
- Insider threats
- Transaction frauds
- Encrypted attacks
- Data exfiltration
- The exploitation of run-time application
- Acquisition of accounts
- Network Lateral Movement
Machines and equipment that may have been attacked to predict, identify and prevent the potential new threats this all can be possible with cyber security analytics. Taken From Article, Challenges and Solutions of Cyber Security Analytics
The primary targets of listed cyber attacks put at risk enterprises, government, military, or other infrastructural assets of a nation or its citizens. The volume and advanced cyber-attacks have increased, as mentioned earlier. These reasons require the incorporation of Artificial Intelligence with existing methods of cybersecurity to appropriately analyze and reduce the occurrence of cyber-attacks.
Why do we need AI Cyber-Security Detection systems?
- The Rule-based detection systems for handling false positive results while handling attacks.
- Hunting of threats efficiently.
- Complete analysis of threat incidents and investigation.
- Threat forecasting
- Retrieve the affected systems, examine the attack's root causes, and improve the security system.
- Monitoring of security.
Key Features of AI-Powered Cybersecurity Systems
The organizations should make sure their AI Cyber Security Tools should have the below-defined core capabilities;
System Security
- Network Security
- Cloud Security
- IoT Security
- Malware
- Autonomous Security
Data Security
- Security Analytics
- Threat Prediction
- ML for Cyber
- Social Network Security
- Insider Attack Detection
Application Security
- FinTech and Blockchain
- Risk and Decision-making
- Trustworthiness
- Data Privacy
- Spam Detection
Cyber Security Analytics Solutions for Enterprises
Cybersecurity Analytics involves aggregating data to collect evidence, build timelines, and analyze capabilities to perform and design a farsighted cybersecurity strategy that detects, analyzes, and mitigates cyber threats.
The AI-enabled cyber security Analytics for Enterprises is defined below.
-
Perspective Analytics: Determination of the actions required for analysis or response.
-
Diagnostic Analytics: Evaluation of root cause analysis and modus operandi of the incidents and attacks.
-
Predictive Analytics: Determination of higher-risk users and assets in the future and the likelihood of upcoming threats.
-
Detective Analytics: Recognition of hidden, unknown threats, bypassed threats, advanced malware, and lateral movement.
-
Descriptive Analytics: This is used to obtain the current status and performance of the metrics and trends.
AI-powered Risk Management Approach to Cyber-security
- Right Collection of Data
- Representation Learning Application
- Machine Learning Customization
- Cyber Threat Analysis
- Model Security Problem
Machines and equipment that may have been attacked to predict, identify and prevent the potential new threats this all can be possible with cyber security analytics. Taken From Article, Application Security – Vulnerabilities Checklist | Tools | Strategy
How do Machine Learning and Deep Learning help in Cybersecurity?
With Machine Learning and Deep Learning, cybersecurity systems can analyze patterns and learn from them to contain similar attacks and respond to altering behaviour. This can help cybersecurity teams be more aggressive in preventing threats and responding to active attacks in real-time.
|
Technique |
Description |
Algorithm |
|
Classification |
This determines whether the security event is reliable and belongs to the group. |
Probabilistic Algorithms such as Naive Bayesian and HMM Instance-based algorithms such as KNN, SVM, and SOM. Neural Networks Decision Trees |
|
Pattern Matching |
Detection of malicious patterns and indicators in large datasets. |
Boyer Moore KMP Entropy Function |
|
Regression |
Determination of trends in security events as well as prediction of the behavior of machines and users |
Linear Regression Logistic Regression Multivariate Regression |
|
Deep Learning |
Creating automated playbooks based on past actions for hunting attacks. |
Deep Boltzmann Machine Deep Belief Networks |
|
Association Rules |
Alerting after detecting similar attackers and attacks. |
Apriori Eclat |
|
Clustering |
Determination of outlier and anomaly. Creation of peer groups of machines and users. |
K-means Clustering Hierarchical Clustering |
|
AI using Neuroscience |
Augmentation of human intelligence, learning with each interaction to proactively detect, analyze, and provide actionable insights into threats. |
Cognitive security |
Therefore, some primary techniques need to be implemented to perform security analytics.
Specialized Knowledge
Security analytics is a complex task that requires specialized knowledge of risk management systems, log files, network systems, and analytics techniques.Opacity
Statistics, machine learning, and mathematics are behind every technique, and once a choice is made, the reasons for choosing a specific technology over others are lost or forgotten. With rules-based systems, the sheer quantity of rules generates a cognitive burden that blocks comprehensive understanding. Finally, these systems' outputs are hard to capture and improve incrementally.
How AI-Driven Analytics Enhances Cybersecurity
Analytics of any kind starts with Data collection. Below are the various data sources from where data is collected and then analyzed.
| Type of Data | Category | Description |
| User Data | UBA Products | Collection and analyzing user access and activities from AD, Proxy, VPN, and applications. |
| Application Data | RASP Products | Calls, data exchange, commands, and WAF data are collected and analyzed to install the agents on the application. |
| Endpoint Data | EDR Products | Installing agents allows you to analyze internal endpoints such as files, processes, memory, registry, connections, and more. |
| Network Data | Network Forensics and Analytics Products | Collecting and analyzing the packets, net flows, DNS, and IPS data by installing the network appliance. |
Performance Attributes Solutions for Cyber Security
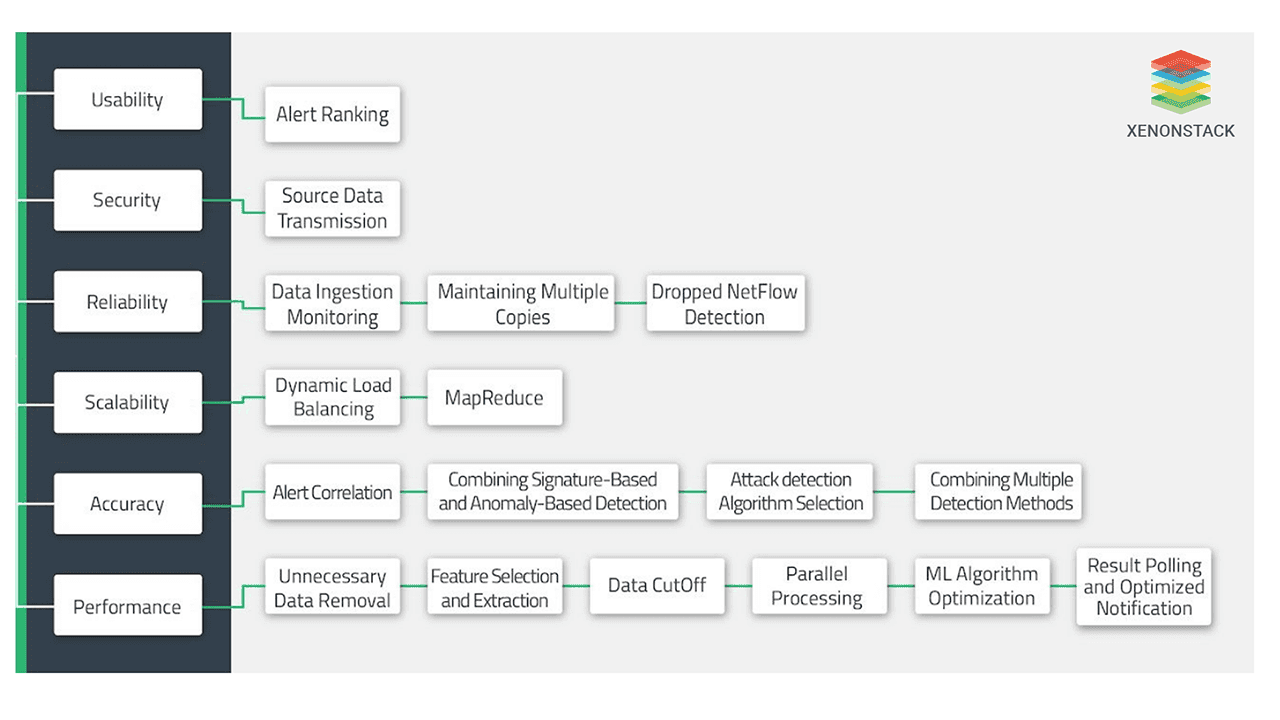 It relates to the performance quality attributes
It relates to the performance quality attributes
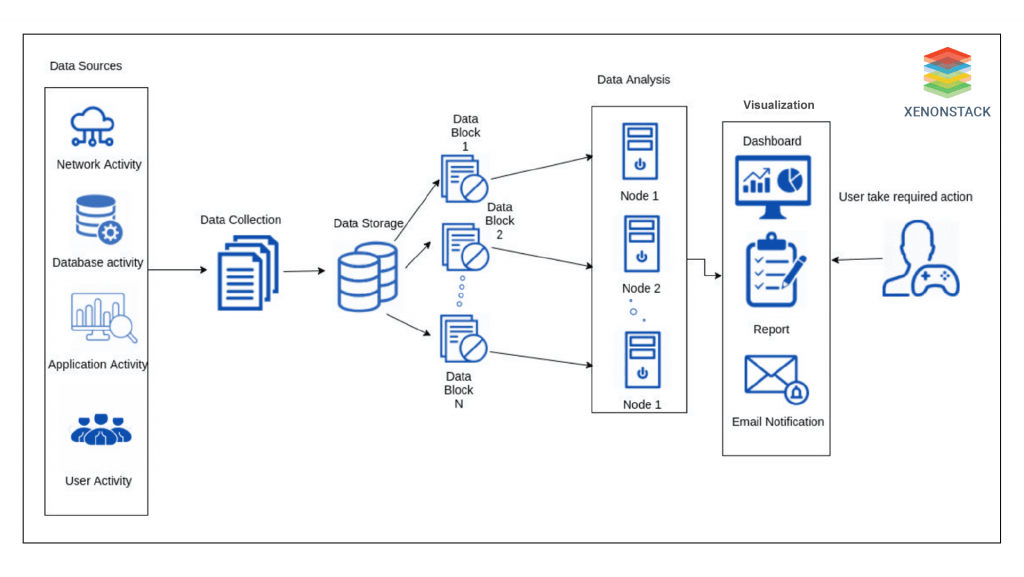
Unnecessary Data Removal
A subset of event data that is not useful for the detection process is considered redundant. Therefore, data is removed to increase performance. As shown in the figure, after removing unnecessary data, the data is forwarded to the data analytics component to detect cyber attacks. Finally, the results are visualized using visualization components.
Feature Extraction and Selection
The feature extraction and feature selection processes allow parallel processing abilities to increase the speed of the selection and extraction process. Then, the extracted feature dataset is forwarded to the data analysis module that performs a different operation to analyse the decrease in the dataset size to identify cyber-attacks. In an attack, alerts are provoked that can be visualized by the user (e.g., network administrator or security expert) using the visualization component. Once these attack alerts come under notice, an enterprise or user can take significant steps to mitigate or prevent the effects of the attack. 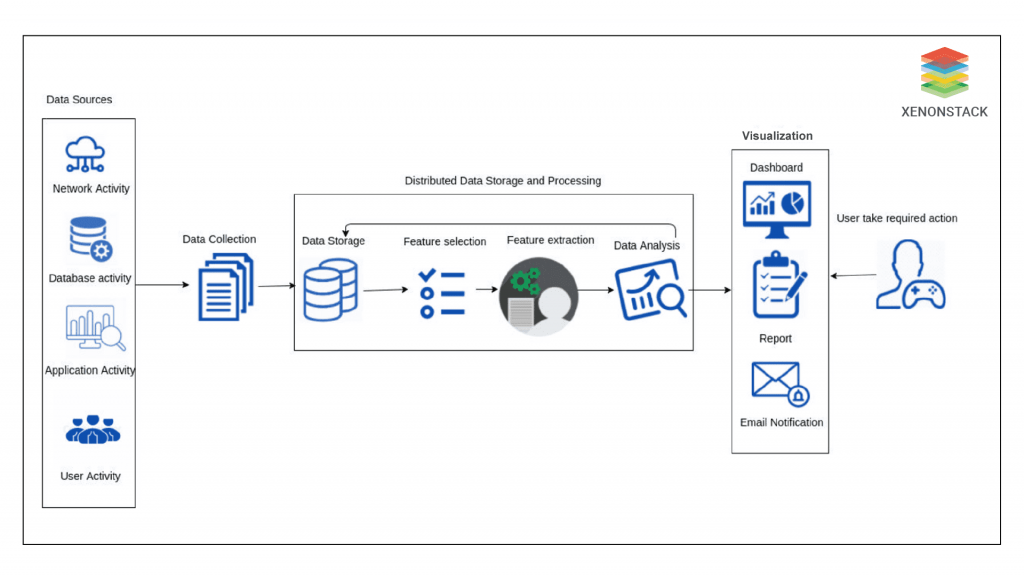 Data Cutoff
Data Cutoff
The data cutoff component imposes the cutoff by neglecting security events that emerge after the connection of a network or process has reached its already defined limit. Any security event that emerges after the predefined limit does not undoubtedly contribute to the attack detection process; therefore, analyzing these types of security events implies an extra burden on data processing resources without any recognizable gain. The data storage entity can store the security event data left after the cutoff. The data analysis module reads the stored data to analyze it and detect cyber attacks. In the end, the analysis results are visualized to a user through a visualization entity, which allows a user to take vital action upon the arrival of every outstanding alert. 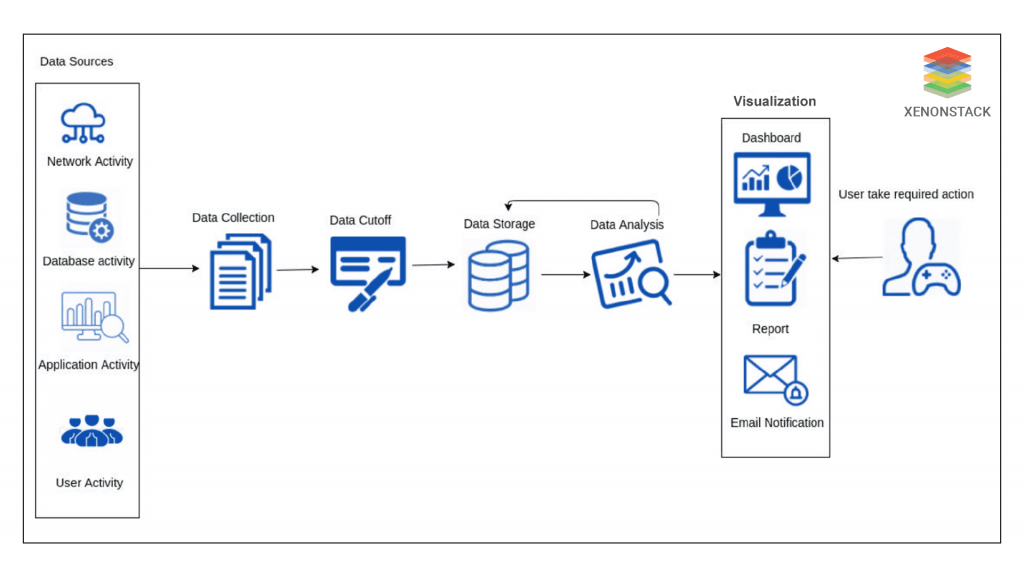 Parallel Processing
Parallel Processing
The data collector entity captures security event data from different resources depending on the different types of security analytics and security requirements of a specific enterprise. The data collector delivers the captured data to a data storage entity, which stores the data. There are many ways to store data, such as Hadoop Distributed File System (HDFS), Relational Database Management System (RDBMS), and HBase. To apply parallel processing, the stored data must be distributed into fixed-size blocks (e.g., 128MB or 64 MB). After partitioning, data is imported into the data analysis component through different nodes working in parallel based on the guidelines of a distributed framework such as Spark or Hadoop. The result received by the analysis is shared with the user through the visualization component.
ML and DL algorithms for Enabling Artificial Intelligence in Cybersecurity
The data collection entity captures security event data for the training process of a security analytics system. The training data can be grabbed from sources within the enterprise where an order is supposed to be deployed.
Today’s customer wants to get detailed insights about the sectors with the most number of attacks, their cost, yearly analysis of security incidents. Taken From Article, Automating AI and ML models in Cyber Security
After gathering the data for training, the data preparation component starts preparing the data for model training by applying various filters. After that, the selected ML algorithm is implemented in the prepared training data to train an attack detection model. The time that is taken by the algorithm to train a model (i.e., training time) alters from algorithm to algorithm. 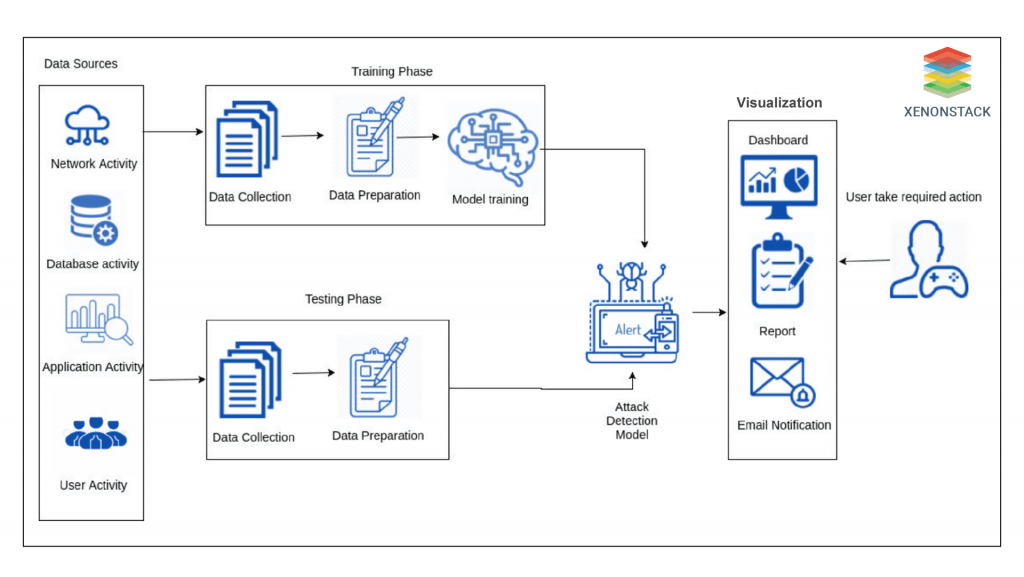 After the model's training, it is tested to investigate whether it can detect cyber attacks. For model testing, data is collected from the enterprise. The data for testing is filtered through the data preparation module and imported into the attack detection model, which is used to analyze the data to identify the attacks based on the rules that are learned during the phase of the training. The time taken by an attack-detecting model to conclude whether a specific stream of data relates to an attack (i.e., decision time) depends upon the implemented algorithm. The result received by the data analysis is visualized to the user through a visualization component.
After the model's training, it is tested to investigate whether it can detect cyber attacks. For model testing, data is collected from the enterprise. The data for testing is filtered through the data preparation module and imported into the attack detection model, which is used to analyze the data to identify the attacks based on the rules that are learned during the phase of the training. The time taken by an attack-detecting model to conclude whether a specific stream of data relates to an attack (i.e., decision time) depends upon the implemented algorithm. The result received by the data analysis is visualized to the user through a visualization component.
Role of Accuracy in Security Models
This section includes accuracy quality attributes:
Alert Correlation
The data collection component grabs security event data from different resources. After that, collected data is stored in the data storage and copied to the data per-processor module to apply pre-processing techniques to the raw data. The pre-processed data is ingested into the alert analysis module, which analyses the data to identify attacks. It is necessary to signify here that the Alert analysis module analyzes the data in a deserted fashion (without seeing any contextual information) anomaly-based or misuse-based analysis or both. The generated alerts are forwarded to the alert verification module, which uses different techniques to identify whether an alert is falsely positive. The warnings identified as false positives are neglected at this level.
The bright and well-arranged alerts are then forwarded to the alert correlation module for further analysis. After that, the alerts are correlated (i.e., logically linked) using different techniques and algorithms, such as rule-based correlation, scenario-based correlation, temporal correlation, and statistical correlation. The Alert correlation module synchronizes with data storage to take the required contextual information about alerts. The results of the correlation are liberated through the visualization module. Finally, an automated response is developed, or a security administrator performs the threat analysis and responds accordingly.
Attacks can originate internally due to malicious intent or negligent actions or externally by malware, target attacks, and APT. Taken From Article, Anomaly Detection for Cyber Network Security
Signature Based Anomaly Detection
The data collection component collects security-relevant data from different resources. After that, the collected data is stored by the data storage module. Next, data is imported into the signature-based detection component that analyses the data to detect attack patterns. For such analysis, this component provides the advantage of the pre-designed rules from the database of the states that identify attack patterns. If any match is detected, an alert is directly generated through a visualization module. 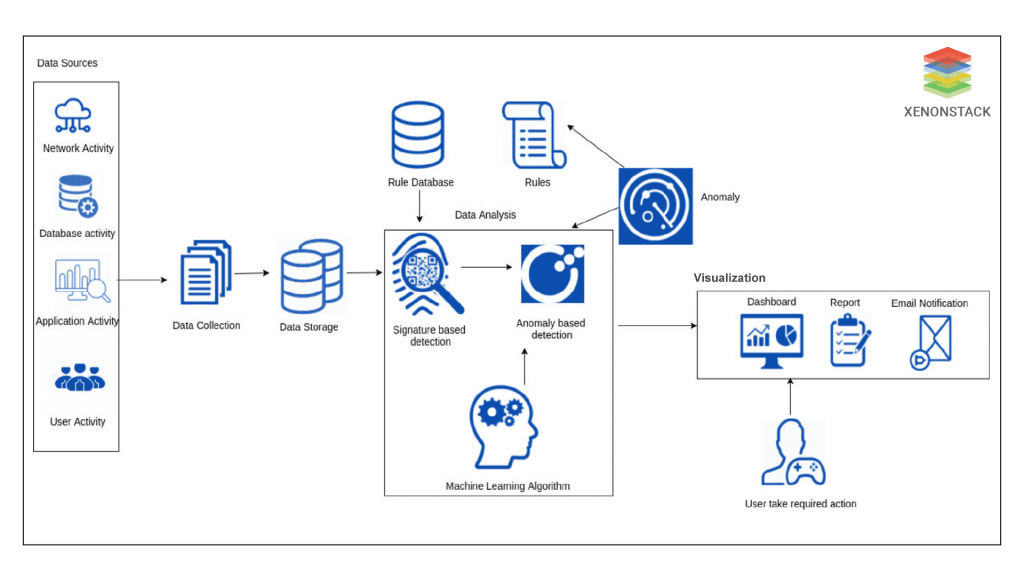 If the signature-based detection component does not identify any pattern of attack in the data, the data is passed to the anomaly-based detection component for detecting unknown attacks that the signature-based detection component cannot identify. An anomaly is defined as the unusual behaviour or pattern of the data. This particular indicates the presence of an error in the system. Taken from Article, Log Analytics, Log Mining and Anomaly Detection with Deep Learning
If the signature-based detection component does not identify any pattern of attack in the data, the data is passed to the anomaly-based detection component for detecting unknown attacks that the signature-based detection component cannot identify. An anomaly is defined as the unusual behaviour or pattern of the data. This particular indicates the presence of an error in the system. Taken from Article, Log Analytics, Log Mining and Anomaly Detection with Deep Learning
The anomaly-based detection module analyzes the data using machine learning algorithms to identify deviations from normal behaviour. When an anomaly (deviation) is identified, an alert is produced through the visualization module. At the same instance of time, the anomaly is defined in the form of an attack pattern or rule and forwarded to the database of the rules. This way, the rules database is continuously updated to enable the signature-based detection component to detect various attacks.
Attack Detection Algorithm
The data collection module grabs security event data to train the security analytic system in detecting cyber attacks. The training data can be collected from different resources within an enterprise where an order is supposed to be deployed. After the data collection process related to the training data, the data preparation module prepares the data for training the model by implying different filters and techniques of feature extraction. 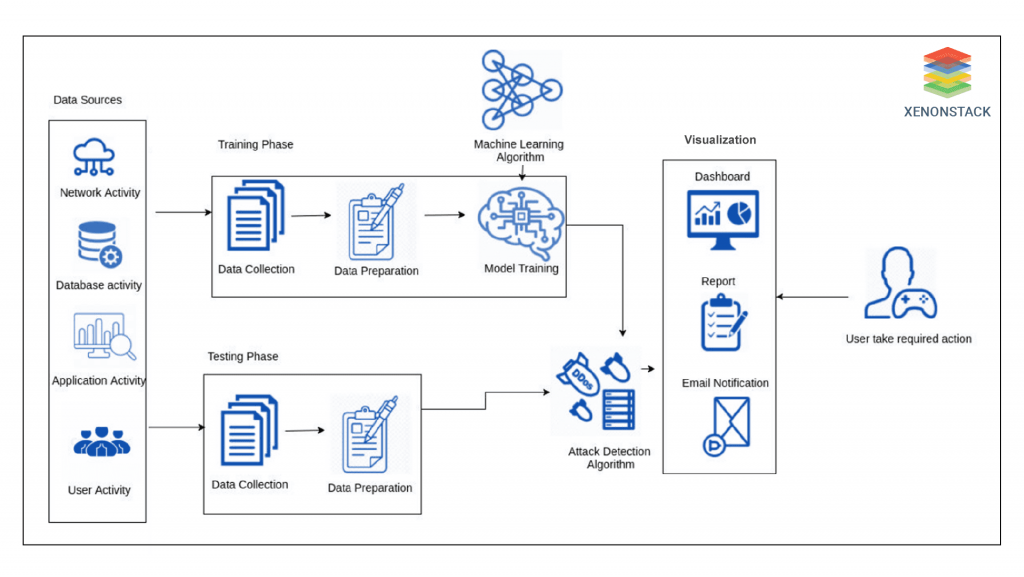 Next, the prepared training data is initialized for the attack detection module. Once the module is prepared, it is validated to investigate whether the model can identify cyber-attacks. The data is collected from an enterprise to validate the model. The test data is prepared for forwarding into the attack detection module. The prepared test data is imported into the attack detection model, which performs the analysis based on the rules learned during the training phase. Here, the imported test data instances are classified as malicious or legitimate. The analysis results are visualized to a user through the visualization module. In a malicious or attack situation, a user can take the required actions immediately, including blocking a few ports or slicing off the affected components from the network to stop further damage.
Next, the prepared training data is initialized for the attack detection module. Once the module is prepared, it is validated to investigate whether the model can identify cyber-attacks. The data is collected from an enterprise to validate the model. The test data is prepared for forwarding into the attack detection module. The prepared test data is imported into the attack detection model, which performs the analysis based on the rules learned during the training phase. Here, the imported test data instances are classified as malicious or legitimate. The analysis results are visualized to a user through the visualization module. In a malicious or attack situation, a user can take the required actions immediately, including blocking a few ports or slicing off the affected components from the network to stop further damage.
Combining Multiple Detection Methods
Security event data is grabbed from different resources. It is important to note that the resources from where security event data can be grabbed are not limited to what is demonstrated in the image. 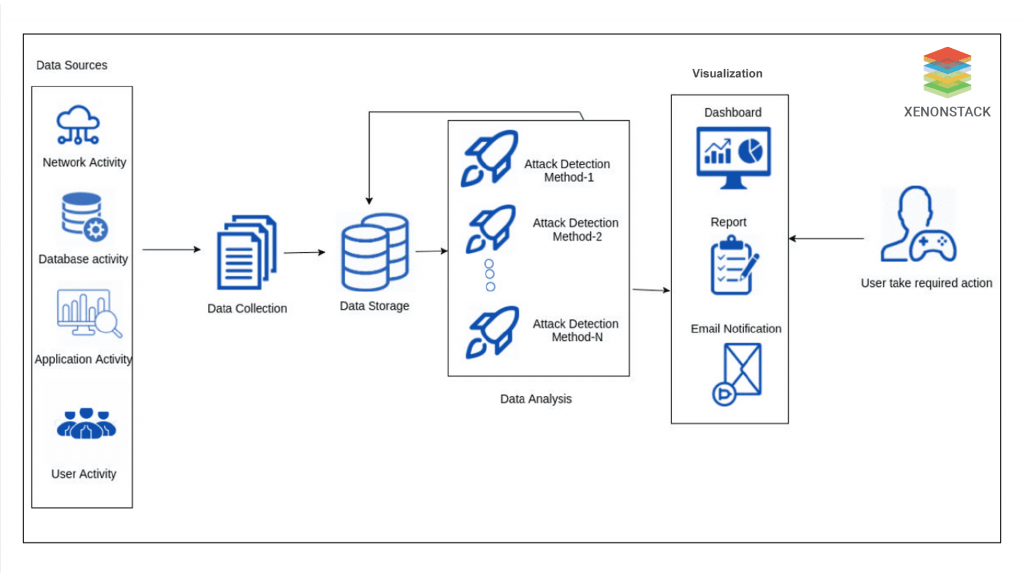 The choice of data resources differs from organization to organization and is based on their security requirements. After completing the collection process, the resulting data is stored in a data storage component. Then, the data is passed to the data analysis component, where different attack detection methods and techniques are implemented to analyze the data. The choices and number of attack detection methods and techniques rely upon some factors.
The choice of data resources differs from organization to organization and is based on their security requirements. After completing the collection process, the resulting data is stored in a data storage component. Then, the data is passed to the data analysis component, where different attack detection methods and techniques are implemented to analyze the data. The choices and number of attack detection methods and techniques rely upon some factors.
These factors comprise the processing ability of an organization, the data resources, security requirements, and finally, the security expertise of the organization. For example, an immensely security-sensitive organization (for example, the National Security Agency) having a high budget as well as the tools of high computational power may incorporate several attack detection methods and techniques to secure their data and infrastructure from attacks related to cyber technologies. The attack detection methods and techniques are imposed on the whole dataset in a parallel manner. The visualization component immediately informs users or administrators of any outstanding anomalies, and they are expected to respond to security alerts.
Almost all organizations are reliable on the Internet for their work. So it becomes a major concern to develop a Unified Cyber Security Monitoring and Management Framework. Taken From Article, Monitoring and Management Framework
Artificial Intelligence Cybersecurity Solutions for Scalability
This section relates to the Reliability quality attribute
Dropped Netflow Detection
The network traffic is fleeting through the router, as the figure demonstrates. A NetFlow grabber is attached to the router, which grabs the NetFlow and stores it in the NetFlow storage. During the NetFlow collection procedure, the NetFlow sequence monitor module monitors the sequence numbers embedded (by design) into the NetFlow.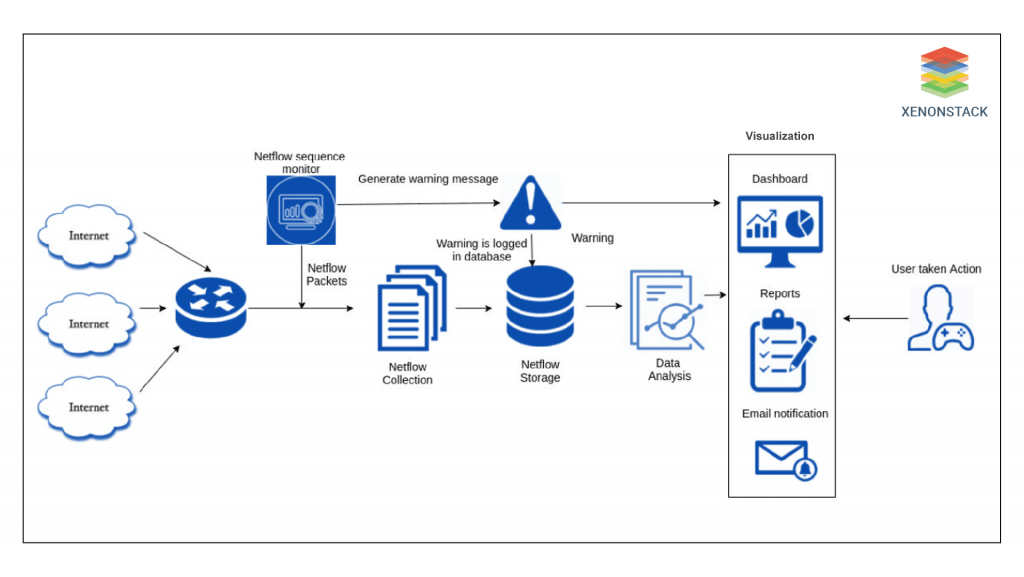 If sequence numbers are found out of order at any stage, the NetFlow sequence monitor sends a warning message representing the missing flow in the particular stream of NetFlow. The warning message is then logged alongside the exact stream in the NetFlow storage module to point out that the stream of NetFlow has some flows missing that might be crucial for identifying an attack. At the same time, a warning is visualized to a security administrator through the visualization module. Then, a security administrator may take immediate action to solve the issue, which may cause some NetFlows to get dropped.
If sequence numbers are found out of order at any stage, the NetFlow sequence monitor sends a warning message representing the missing flow in the particular stream of NetFlow. The warning message is then logged alongside the exact stream in the NetFlow storage module to point out that the stream of NetFlow has some flows missing that might be crucial for identifying an attack. At the same time, a warning is visualized to a security administrator through the visualization module. Then, a security administrator may take immediate action to solve the issue, which may cause some NetFlows to get dropped.
- Check out the Generative AI Solutions at xenonstack.ai.
AI Measures for Strengthening Cybersecurity
The nodes used for collecting security event data are placed in different sectors for collecting data types. Some collect data related to network traffic, and others collect database access information, and so on. Security measures are implemented for the data collected to ensure its secure transfer from the data collection module to the data storage and analysis module. The security measures incorporated differentiate from system to system. 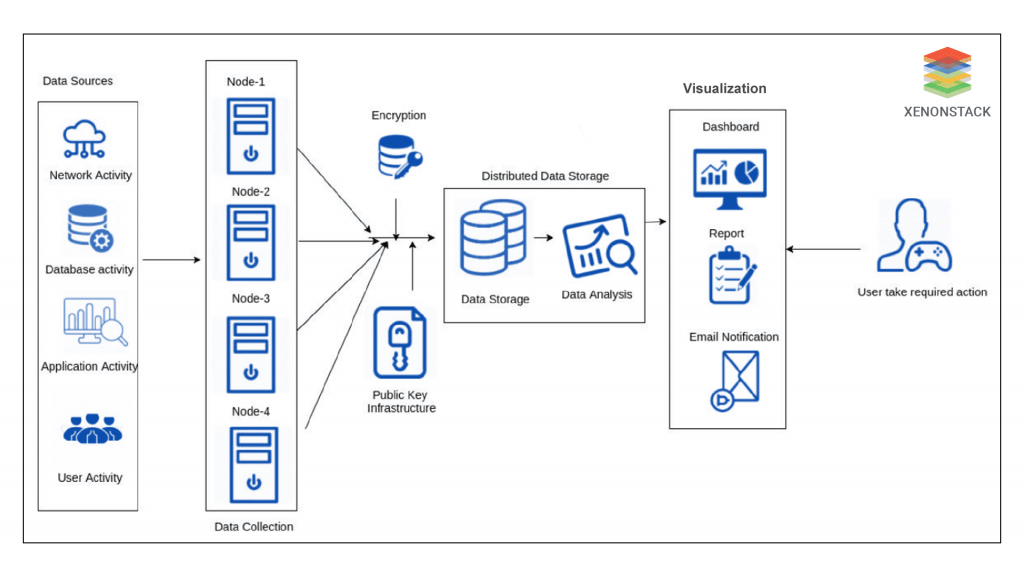 Some systems give preference to encrypt the collected data and then perform the transfer process of the data in encrypted form. Other systems prefer to use Public Key Infrastructure (PKI) to ensure a secure data transfer process and verification of the party transferring the data. As soon as the data is received by the data storage module and analysis module in a secure mode, the data analytic operations are applied to perform analysis processes to detect attacks. The results generated from the analysis are presented to users through the visualization component.
Some systems give preference to encrypt the collected data and then perform the transfer process of the data in encrypted form. Other systems prefer to use Public Key Infrastructure (PKI) to ensure a secure data transfer process and verification of the party transferring the data. As soon as the data is received by the data storage module and analysis module in a secure mode, the data analytic operations are applied to perform analysis processes to detect attacks. The results generated from the analysis are presented to users through the visualization component.
Artificial Intelligence Cybersecurity Alert Ranking Modules
The data collection module grabs security event data from different resources, which is then pre-processed by the pre-processing data module. The pre-processed security event data is passed to the data analysis component, which performs different analytical procedures on the data to identify cyber-attacks. The results exported from the analysis (i.e., alerts) are passed to the alert ranking module, which ranks the alerts based on predefined rules to assess the impact of the alert on the whole organization’s infrastructure. The criterion for ranking the alerts relies on the organization. 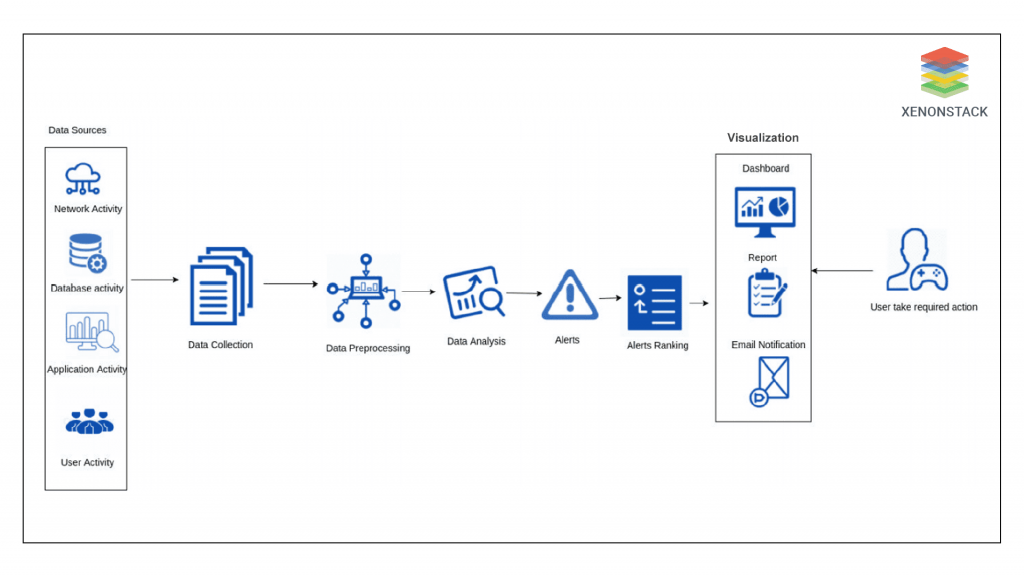 For example, the ranking rules for an organization vulnerable to DoS attacks will rely on an organization vulnerable to brute force attacks. Finally, the ranked list of easy-to-interpret and straightforward alerts is shared with security administrators using the visualization module, which eases the task of a security administrator to first give a response to the alerts on the utmost of the rank list as these alerts are foreseen to be more consequential and dangerous.
For example, the ranking rules for an organization vulnerable to DoS attacks will rely on an organization vulnerable to brute force attacks. Finally, the ranked list of easy-to-interpret and straightforward alerts is shared with security administrators using the visualization module, which eases the task of a security administrator to first give a response to the alerts on the utmost of the rank list as these alerts are foreseen to be more consequential and dangerous.
Top Tools for AI in Cybersecurity
These are some of the tools that use various AI algorithms to provide the best security to organizations.
-
Symantec's Targeted Attack Analytics—This tool uncovers private and targeted attacks. It applies Artificial intelligence and machine learning to the processes, knowledge, and capabilities of Symantec's security experts and researchers. Symantec used the Targeted Attack analytics tool to counter the Dragonfly 2.0 attack. This attack targeted multiple energy companies in the USA and tried to gain access to operational networks.
-
Sophos' Intercept X tool - Sophos is a British software and hardware security company. Intercept X uses a deep-learning neural network that functions like a human brain. Before a file is performed, Intercept X will retrieve millions of features from a file, perform an in-depth review and decide whether a file is benevolent or harmful within 20 milliseconds
-
IBM QRadar Advisor—IBM's QRadar Advisor uses IBM Watson technologies to counter cyber-attacks. It uses AI to auto-examine signs of vulnerability or exploitation. QRadar Advisor also uses cognitive reasoning to provide valuable feedback and speed up the response process.
-
Vectra's Cognito - Vectra's Cognito detects attackers in real time using AI. This tool automates threat detection and identification. Cognito collects logs, cloud events, network usage data, and behavioural detection algorithms to reveal hidden attackers in workloads and IOT devices.
-
Darktrace Antigena - Darktrace is an effective method of self-defence. Antigena extends the critical functionality of Darktrace to recognize and duplicate the role of digital antibodies that recognize and neutralize threats and viruses. Antigena utilizes the Enterprise Immune System of Darktrace to recognize and react to malicious behaviour in real-time based on the nature of the danger.
Future Trends of AI in Cybersecurity
Enhanced Threat Detection
AI will improve real-time threat detection by analyzing large data sets to identify patterns and anomalies
Automated Incident Response
AI will automate responses to threats, such as isolating systems, reducing response times and minimizing damage
User Behavior Analytics
Monitoring user behavior with AI will help detect unusual activities that may indicate breaches or insider threats
Predictive Analytics
AI will use historical data to predict future threats, allowing organizations to strengthen defenses proactively
- Learn more about The Ethics of Artificial Intelligence
- Read more about Impact of Insider Threats in Cyber Security
- Explore more about the Cyber Security Checklist for 2024
- Read more about Adaptive Security