Autonomous Security Agents
AI agents are computational entities that exhibit intelligent behavior through autonomy, reactivity, proactiveness, and social ability. They interact with their environment and users to achieve specific goals by perceiving inputs, reasoning about tasks, planning actions, and executing tasks using internal and external tools.
Custom AI agents, powered by large language models like GPT-4, have revolutionized healthcare, finance, customer service, and agent operating systems tasks. However, their increased sophistication brings new security challenges.
Security AI Agents aim to protect users from vulnerabilities and threats that could compromise functionality, integrity, and safety. This includes securely handling user inputs and interactions without being susceptible to attacks.
Knowledge Gaps lead to security challenges
The main knowledge gaps leading to these security challenges are the unpredictability of multistep user inputs, complexity in internal executions, variability of operational environments, and interactions with untrusted external entities.

Knowledge Gaps lead to security challenges
-
In Gap 1, the unpredictability of multi-step user inputs plays a crucial role, as users influence AI agents throughout task execution with their feedback. However, inadequately described user inputs and the presence of malicious users can lead to potential security threats. Therefore, ensuring the clarity and security of user inputs is crucial to maintaining AI agents' effective and safe operation.
-
In Gap 2, the complexity of internal executions poses a challenge as many internal execution states are implicit, making it difficult to observe detailed internal states. This can result in undetected security issues, highlighting the need to audit the complex internal execution of AI agents.
-
Gap 3 pertains to the variability of operational environments. Many agents' development, deployment, and execution phases span various environments, leading to inconsistent behavioral outcomes. Securely completing work tasks across multiple environments is a significant challenge.
-
In Gap 4, interactions with untrusted external entities present a crucial capability as AI agents must teach large models how to use tools and other agents. However, assuming a trusted external entity in the interaction process can lead to various attack surfaces. Interacting with untrusted entities presents a challenge for AI agents.
Autonomous AI Agent as a SOC Analyst
Autonomous SoC
SOC stands for Security Operations Center, a centralized unit for security operations in a company. Every company builds a SOC team whose main aim is to monitor, analyze, and protect the company and its assets from security threats such as cyber-attacks, data threats, viruses, malware, etc.
Role of SOC Analyst
-
Monitoring and Detection: SOC analysts continuously monitor network and system activity to detect malicious behavior and potential threats. They use various tools such as SIEM (Security Information and Event Management) systems, IDS (Intrusion Detection Systems), and IPS (Intrusion Prevention Systems) to gather and analyze data.
-
Incident Response: Investigate and mitigate detected security incidents to minimize impact.
-
Threat Analysis: Analyze threats to understand attack methods and affected systems.
-
Reporting: Create detailed reports on incidents and security breaches.
-
Improving Security Measures: Enhancements to security policies and tools based on threat analysis are recommended.
-
Compliance and Auditing: Ensure adherence to security regulations and participate in audits.
-
Communication and Collaboration: Coordinate with IT (Information Technology) and security teams to manage and respond to security issues.
Solution Approach: Autonomous AI Agents as a SOC Analyst
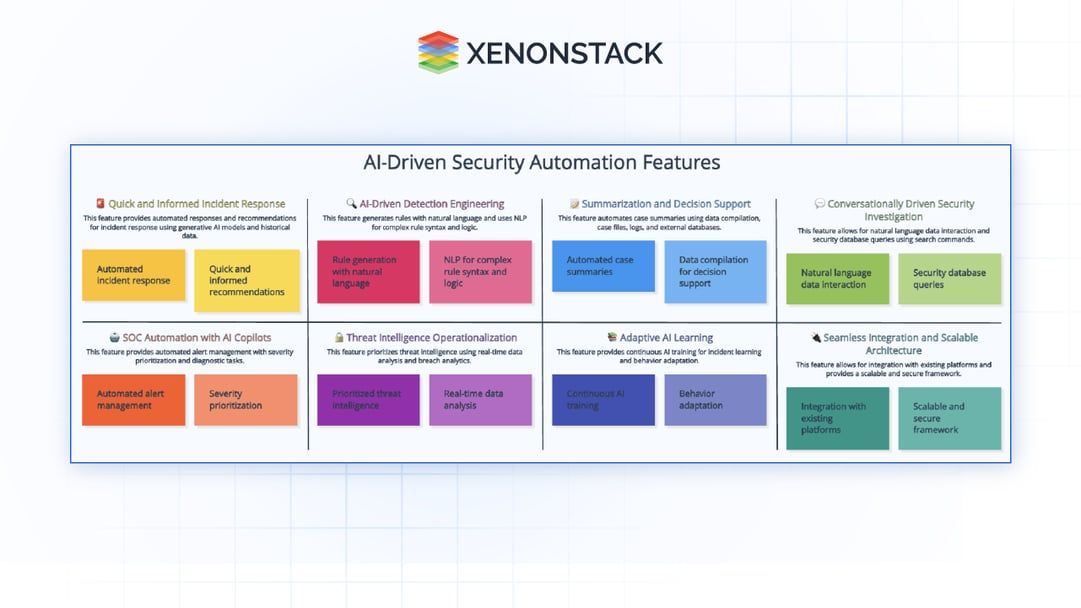
1. Quick and Informed Incident Response
-
Automated Responses and Recommendations: Generative AI models will analyze incoming alerts and use historical data to predict the most effective response strategies. These models will instantly generate actionable recommendations and automated responses for SOC analysts, reducing response times and enhancing accuracy.
2. AI-Driven Detection Engineering
-
Rule Generation with Natural Language: The AI employs advanced NLP (Natural Language Processing) techniques to translate plain language inputs into sophisticated detection rules. This allows analysts to express their requirements conversationally while the AI handles the complex rule syntax and logic.
-
Refine and Score Detections: AI will monitor the effectiveness of these rules in real time, suggesting refinements and recalibrating risk scores based on outcomes and evolving threat intelligence.
AI-Driven Security Automation
3. Summarization and Decision Support
-
Automated Case Summaries: Generative AI will automatically compile data from various sources into concise summaries. Analyzing case files, logs, and external databases will present a synthesized overview of each incident, highlighting key details that inform decision-making.
-
Customizable Detail Levels: Based on user feedback, the AI will offer options to adjust the level of detail, providing either a broad overview or a deep dive into specific aspects of the incident as required.
4. Conversationally Driven Security Investigation
-
Natural Language Data Interaction: Generative AI will allow analysts to query security databases using natural language, making the investigation process as simple as searching on the internet. The AI will interpret the queries, generate the necessary search commands, and retrieve relevant data.
-
Iterative Query Adjustment: As analysts receive initial results, they can refine their queries through simple commands, prompting the AI to delve deeper or alter the focus of the investigation, tailoring the exploration process to their precise needs.
5. SOC Automation with AI Copilots
-
Automated Alert Management: AI copilots will automatically categorize and prioritize alerts based on their severity and potential impact, handling initial diagnostic tasks to determine the most appropriate responses.
-
Contextual Threat Attribution: The AI will enrich alerts with contextual data, identifying and correlating threat actors and their methods by analyzing patterns and historical data. This will give analysts a clearer understanding of the nature of the threat and suggested countermeasures.
6. Threat Intelligence Operationalization
-
Prioritized Threat Intelligence: AI models will analyze incoming threat intelligence from multiple sources, identifying and prioritizing the most relevant and pressing indicators of compromise based on current network activity and threat landscapes.
-
Enhanced Breach Detection: By integrating priority scores and real-time data analysis, AI-driven breach analytics will highlight anomalies and patterns indicative of a breach, focusing analyst attention where it is most needed.
7. Adaptive AI Learning
-
Continuous AI Training: Generative AI models will continuously learn from new incidents, analyst interactions, and evolving threats, adapting their behaviors and recommendations to improve precision and effectiveness over time.
8. Seamless Integration and Scalable Architecture
-
Integration with Existing Platforms: The AI features will be designed to integrate seamlessly into existing SOC platforms, maintaining user interface continuity and minimizing disruption.
-
Scalable and Secure Framework: The architecture will be robust and flexible, designed to scale with the organization's needs and secure against external attacks and internal vulnerabilities.
Future of Autonomous SoC
An autonomous AI Agent as a SOC Analyst reflects an innovative approach to enhancing security operations. By automating the detection, analysis, and response to security threats, generative AI significantly amplifies the efficiency and effectiveness of Security Operations Centres. This represents a promising step in the ongoing endeavor to safeguard digital and real-world assets against the constantly evolving landscape of cyber threats. Moving forward, the focus should remain on refining AI technologies to ensure they can securely navigate cyberspace's sophisticated and unpredictable terrain, ultimately fostering a safer, more resilient digital ecosystem.
Next Steps with Security AI Agents
Talk to our experts about implementing compound AI system, How Industries and different departments use Agentic Workflows and Decision Intelligence to Become Decision Centric. Utilizes AI to automate and optimize IT support and operations, improving efficiency and responsiveness.
.webp?width=1921&height=622&name=usecase-banner%20(1).webp)



