The Open Policy Agent (OPA)
The Open Policy Agent (OPA) is an open-source, general-purpose policy engine that unifies policy implementation across the stack. It provides a high-level declarative language that lets us specify policy as code and simple APIs to offload policy decision-making from your software. You can use OPA to enforce policies in microservices, Kubernetes, CI/CD pipelines, API gateways, and more.Integrate Open Policy Agent with Cloud Native Services
Open Policy Agent can be integrated as a sidecar, host-level daemon, or library. Services offload policy decisions to OPA by executing queries. OPA evaluates policies and data to produce query results (which are sent back to the client). Steps to integrate OPA with a service:-- Create policy using REGO (OPA native query language). For detailed information on Rego, see the Policy Language documentation.
- Test Policy against an example dataset using OPA CLI command $opa eval.
- Save policy in the OPA server.
- Use Rest APIs to integrate it with an application.
- Or use the Golang library to integrate it with a golang application
- Or use the OPA gatekeeper to integrate it with Kubernetes.
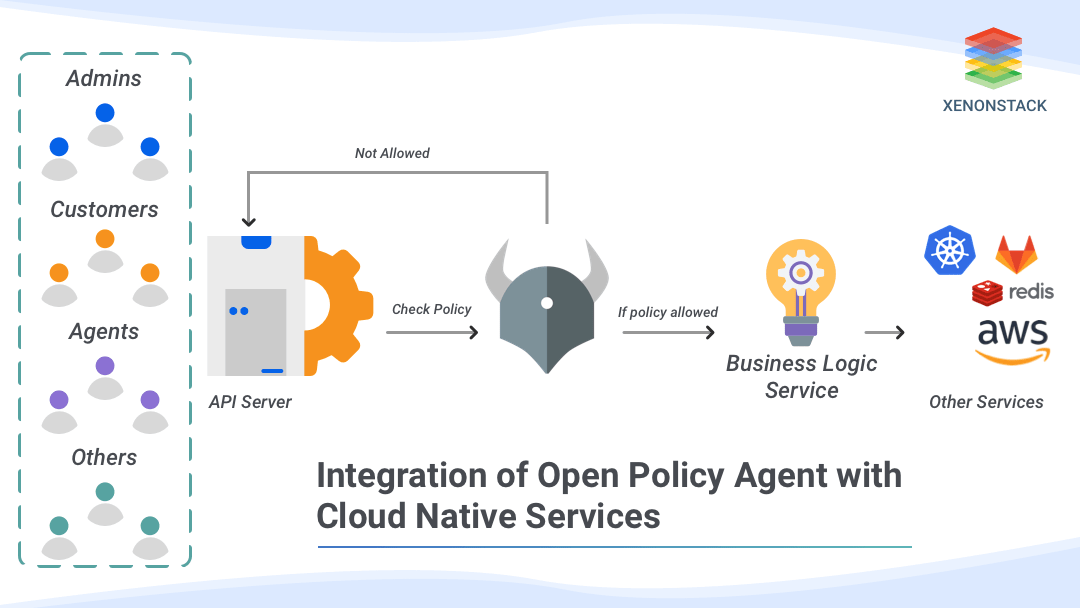
How does Open Policy Agent work?
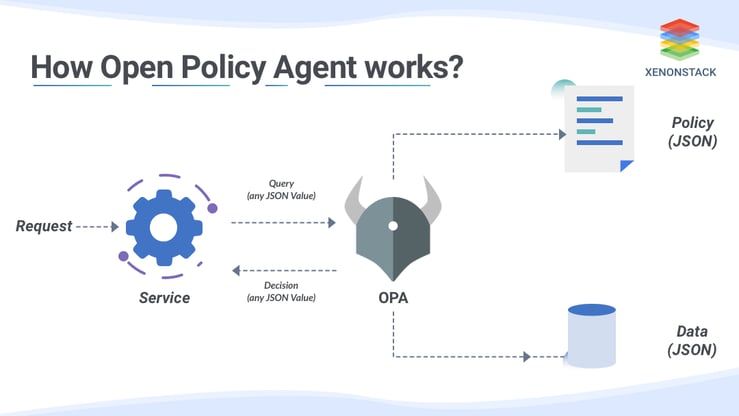
After integrating the OPA service with your application service, each application service request or event will go through OPA service first for policy verification. Steps for policy verification:-- A query is sent to the OPA service in JSON format.
- Above query is processed by OPA against a policy written in rego language.
- After processing output is generated in json format known as a decision.
Where can Open Policy Agent be used?
OPA policy decisions are not limited to a simple yes/no or allow/deny answers. Like query inputs, your policies can generate arbitrary structured data as output. OPA and Rego are domain-agnostic so that you can describe almost any invariant in your policies. For example:- Mapping users and resources.
- Cloud Native Network related policies. (Ex. Which subnets egress traffic is allowed )
- Mapping cluster and workloads.
- Define the registered path for downloading executable binaries.
- Container related policies. (Ex. A container can execute with which OS capabilities)
- Mapping system access time with the usability of the system
Empowering enterprises with Cloud Native Solutions to Build, Run and Operate applications faster Cloud Native Application Development Services
Conclusion
In addition to all the features, OPA has REPL (Read-Eval-Print Loop) that can be used to learn, build, collaborate, and host all in one place. REPL has a complete set of testing tools to ensure policies can be built, breaking part of a continuous integration pipeline. It also has a VScode plugin that highlights, evaluates, and queries policies in Integrated Development Environment.
- Explore about Cloud Native Architecture Patterns and Design
- Comprehend the Cloud Native Storage Solutions
- Learn about the Cloud Native Network Functions