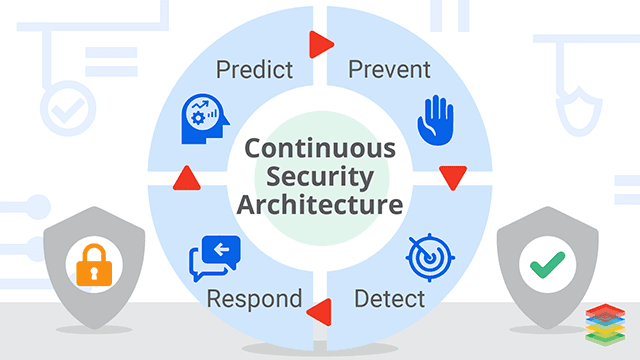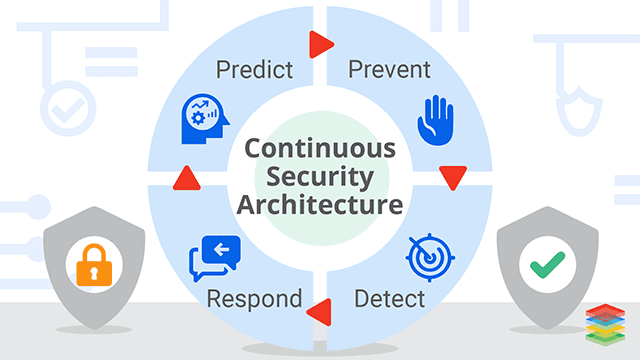
Introduction to Continuous Security and Its Importance
As organizations increasingly adopt DevOps practices, the need for robust continuous security measures has never been more critical. Integrating security into every development lifecycle phase is essential in a landscape where cyber threats are constantly evolving. Constant security monitoring helps identify vulnerabilities early and ensures security is a shared responsibility among all team members. This blog delves into the myths surrounding DevSecOps, explores practical applications of continuous security, and highlights its importance in safeguarding modern applications.
What is Continuous Security?
Continuous security is making security a part of the CI/CD process. Most organizations, especially high-performing ones, have already implemented CI/CD pipelines to make software releases more agile. These pipelines build software automatically using continuous integration tools, package it in docker images, and run the containers in production using continuous deployment tools such as Jenkins and Kubernetes.
Applying all DevOps values to software security ensures that safety verification becomes an active and integrated part of the existing development process. Continuous security works alongside the continuous everything process and makes continuously securing our software and infrastructure.
DevOps Security focuses on the point of delivering secure software using continuous delivery architectures. Click to explore about our, DevSecOps and Continuous Security For an Enterprise
The Importance of Continuous Security for Modern Operations
Infrastructure complexity and frequent changes make continuous security practices crucial in modern applications, especially those built on microservices and deployed on Docker and Kubernetes platforms.
-
Continuous security ensures end-to-end protection by continuously monitoring and addressing vulnerabilities at each stage of development, deployment, and operations.
-
Security breaches are a significant threat, highlighting the need for continuous security monitoring and scanning throughout the software lifecycle.
-
Implementing continuous integration (CI) and continuous delivery (CD) pipelines enhances development speed, but strong security controls must complement these benefits at every stage.
-
Continuous security ensures security is embedded into CI/CD pipelines, enabling security automation and constant improvements in data protection.
-
Organizations can build consumer trust by protecting sensitive data and maintaining security during development.
Artificial intelligence is revolutionizing cybersecurity by enhancing threat detection, automation, and response. With AI, organizations can proactively identify vulnerabilities, reduce risks, and respond swiftly to evolving cyber threats.
How Continuous Security Enhances Threat Detection and Response?
Continuous Security adds an extra layer of protection over DevOps processes and pipelines to ensure that all underlying infrastructure and applications are free from vulnerabilities and risks. This is particularly crucial in cloud-native applications, which support microservices' high availability and resiliency through service discovery and load balancing across stateless application containers. By embedding continuous security across containers, organizations ensure that their applications are monitored and secured throughout their lifecycle, with runtime security tools actively identifying and mitigating risks continuous testing vs continuous integration.
The DevOps movement has introduced processes like continuous integration (CI) and continuous delivery (CD), which streamline the rapid delivery and testing of code during development. Continuous security enhances these processes by injecting security policies and conducting penetration testing of software applications using agile methodologies.
The DevSecOps philosophy ensures that security is built into the product, unlike traditional InfoSec, which often tests for security only at the end of the development process. With continuous security, vulnerabilities are detected early and resolved through security scanning integrated within the CI pipeline, allowing for automatic detection and fixing of issues in real time. This approach ensures that security is not an afterthought but a continuous, evolving process, with feedback loops that make ongoing improvements to the overall security posture of the application.
A type of software testing that ensures that any application or system is free from threats, vulnerabilities, and risks. Taken From Article, Security Testing in DevOps
Image
Dockerfiles are treated as Blueprints for building Docker images. They are put in VC, such as Git. Always Be explicit with versions; don't use the latest. Try to keep a minimum number of layers.
Container
Containers are treated as immutable. There is a separation between code, config, and data.
Registry Security
Private registries are hosted to store Docker images privately. They have proper image signing, which validates what's inside the image and what version it is running.
Underlying Host Security
Kernel features such as groups, and Namespaces provide resource and process isolation features. Containers running on a host assume that the underlying host has proper security. The container uses SELinux for mandatory access controls. Read-only mounts are enabled from the host to the running container.
Isolation of Network
Network namespaces enable it and provide resource isolation. Multiple environments are used for DEV, UAT, and PROD. Kubernetes network policies allow traffic from the same namespace only, thus restricting the area of access continuous testing in agile.
A process that continuously searches the web applications and the IT infrastructure for possible vulnerability and security risks. Click to explore about, Continuous Security Testing
Debunking Common Myths about DevSecOps and Security
DevSecOps is often misunderstood, leading to several myths that can hinder its effective implementation. Here are some common misconceptions:
-
Myth: DevSecOps is solely the responsibility of the security team.
Reality: DevSecOps emphasizes that security is everyone's responsibility within the development lifecycle. This approach ensures that all team members, from developers to operations, are engaged in continuous security practices and understand their role in maintaining security.
-
Myth: Implementing DevSecOps slows down development.
Reality: While integrating security into the CI/CD pipeline may seem to add overhead, it streamlines processes by addressing vulnerabilities early through continuous security testing and automation. This proactive approach can lead to faster delivery times and reduced technical debt.
-
Myth: DevSecOps is only about tools and technology.
Reality: Although tools like Security Information and Event Management (SIEM) and Runtime Security Tools are essential, the success of DevSecOps relies heavily on culture and team collaboration. Effective DevSecOps Strategies involve fostering a culture where security is integrated into every development phase.
-
Myth: Continuous Security is just a checkbox activity.
Reality: Continuous Security requires ongoing effort and commitment to monitoring and improving security measures throughout the software lifecycle. It involves practices such as continuous cybersecurity monitoring and regular vulnerability assessments.
-
Myth: DevSecOps is only relevant for large organizations.
Reality: Organizations of all sizes can benefit from adopting DevSecOps principles. Small teams can implement DevOps Security practices to enhance their security posture without significant resource investment.
How to Enable Continuous Security?
Continuous security can be enabled in the following ways:
- Implement gradual changes into the existing DevOps pipeline, keeping security in mind.
- Tools such as Vault should be used for certificate stores with M-TLS for encryption.
- Leverage various existing security tools & automation to enable DevSecOps in the organization.
- Put metrics and alerts on all security incidents, whether they are related to Infrastructure or applications.
- Find attack vectors' potential effects of the security holes & Fixing them in automated ways.
Key Benefits of Adopting Continuous Security Practices
-
Reduce Risks: Continuous security helps identify and address vulnerabilities early, reducing the chances of security breaches through continuous cybersecurity and vulnerability management monitoring.
-
Lower Costs: Continuous security testing lowers the costs of breach recovery, compliance penalties, and reputational damage by detecting and fixing vulnerabilities early.
-
Speed Delivery: Continuous security integrated with CI/CD pipelines speeds up development and deployment by automatically identifying and resolving vulnerabilities, enabling faster time-to-market.
-
Speed Reaction: Incident response is faster with continuous security monitoring, allowing quick detection and mitigation of threats to minimize potential damage.
-
Scalability: As applications scale, continuous security ensures security practices evolve, protecting growing infrastructures, microservices, and cloud-native applications.
-
Availability and Resiliency: Continuous cloud security ensures high availability and operational resiliency by maintaining security throughout the application lifecycle, preventing disruptions.
-
Local Service Discovery: Local service discovery ensures apps are accessed only within a secure cluster, enhancing data protection and minimizing external threats.
DevOps assembly lines are targeted on automating and connecting activities performed by several groups part of software development phases Source- DevOps Assembly Line
Best Practices for Continuous Security in DevOps Pipeline
The following best practices are essential for implementing continuous security in a DevOps pipeline. Security should never be an afterthought; it must be embedded from the inception of an idea to production. Below are key practices for ensuring security automation and testing are effectively applied across the pipeline.
-
Always run as a regular user: Avoid running containers as root to minimize security risks. This helps enforce security controls and reduces the attack surface.
-
Define resource requests and limits: Set resource requests and limits for containers to prevent resource exhaustion attacks and ensure workloads are efficiently managed.
-
Enable logging: Logging should be enabled to track activities and detect potential security issues. It is essential for incident response and continuous monitoring.
-
Balance simplicity and security: A balance between user-friendly interfaces and robust security must be achieved. While UI designers may prioritize simplicity, InfoSec must ensure data protection and cybersecurity measures are in place.
-
Focus on people and culture first: Cultivate a security-first culture across teams by prioritizing security training and awareness at all levels.
-
Then, focus on processes: Establish continuous security practices and automate security policies within the DevOps pipeline to align with DevSecOps strategies.
-
Finally, focus on tools: Implement the right security tools to automate security scanning, threat detection, and vulnerability management. These tools should integrate seamlessly into the pipeline and continuously improve security practices.
Top Tools for Implementing Continuous Security Effectively
-
Sysdig Secure: A comprehensive tool for container security that provides real-time threat detection and vulnerability management for Kubernetes, cloud, and containerized applications.
-
Mittn: Offers continuous security monitoring and risk management with real-time security scanning and vulnerability assessments during development and production.
-
Signal Sciences: Provides runtime security tools for threat detection at the application layer, utilizing machine learning for real-time insights without compromising performance.
-
Logging—Kibana + Elasticsearch: This combination enables powerful security logging and monitoring, allowing teams to aggregate and visualize security data for incident response and quick issue resolution.
-
Monitoring—Prometheus with Grafana: This solution offers continuous monitoring and real-time security insights. Prometheus collects metrics, and Grafana visualizes them for proactive security management.
-
OWASP Zed Attack Proxy (ZAP): An open-source tool for penetration testing that helps identify security flaws in web applications early in the development lifecycle.
Real-World Applications and Use Cases of Continuous Security
Continuous security has become a cornerstone in modern software development, particularly within DevSecOps frameworks. Here are several applications and use cases:
-
Cloud Environments: With the rise of continuous cloud security, organizations leverage automated tools for real-time threat detection and compliance monitoring across cloud infrastructures, ensuring that applications remain secure throughout their lifecycle.
-
CI/CD Pipelines: Integrating security into CI/CD pipelines allows for automated security scanning during each stage of development, enabling teams to identify and remediate security flaws early in the process.
-
Application Security: Continuous security practices help organizations maintain robust application security by implementing regular testing protocols, such as penetration testing and vulnerability management, ensuring that applications are resilient against threats.
-
Incident Response: Continuous monitoring enables rapid incident response by providing real-time alerts on potential breaches or vulnerabilities, allowing teams to act swiftly to mitigate risks.
-
Regulatory Compliance: Organizations can utilize continuous security to ensure adherence to compliance standards by automating audits and maintaining detailed logs of security controls, which is crucial for industries like finance and healthcare.
-
Security Training: By fostering a culture of security awareness through ongoing training programs, organizations empower their teams to recognize potential threats and adhere to best practices in cybersecurity.
-
Breach and Attack Simulation: Continuous security also includes conducting regular breach simulations to test the effectiveness of existing security measures. This allows teams to refine their incident response strategies based on real-world scenarios.
Building a Comprehensive Strategy for Continuous Security
Adopting cloud infrastructure demands a new approach to testing and validation within the CI/CD pipeline, highlighting the need for agile teams to adopt new practices that enable faster progress — namely, the DevOps model. As development speeds up, ensuring secure deployments becomes critical, making continuous security an essential component of the process. By integrating continuous security into every stage of development, from code creation to production, organizations can safeguard their systems while maintaining agility and speed.
Next Steps for Implementing Continuous Security
Connect with our experts to explore how AI-driven systems can optimize DevOps security. Learn how various industries leverage Agentic Workflows and Decision Intelligence to become more agile and security-centric. By integrating AI, businesses can automate and enhance security operations, boosting efficiency, and ensuring real-time, proactive threat detection and response across microservices and IT environments.